Bridging CISO and CTO Relationships: The Operating Rhythm That Ends Security vs Speed
Fix CISO and CTO Relationships with a simple operating rhythm, shared metrics, and decision rights so you ship faster with fewer risk surprises.


You're trying to ship product fast, keep systems reliable, and avoid risks that could've been prevented. Yet the moment a release gets tense, the same story shows up: the CTO pushes for delivery, the CISO pushes for safety, and everyone else feels stuck in the middle.
That "security vs speed" fight usually isn't about attitude. It's about organizational silos in CISO and CTO relationships running on different incentives, different language, and unclear decision rights. Security hears "we'll fix it later" and sees future harm. Engineering hears "we need a review" and sees a delay.
You can stop treating this like a personality problem. What you need is a simple operating rhythm: a repeatable cadence, a few shared artifacts, and clear decision rules. When you run that rhythm, you make tradeoffs early, decide faster, and reduce rework that wrecks predictability.
Key takeaways you can apply this quarter
Align on shared outcomes (trust, uptime, revenue protection), not competing agendas.
Use shared KPIs with a few joint metrics, tracked monthly.
Hold a weekly 30-minute risk and delivery sync, a key part of the risk management process, to clear blockers and approve exceptions.
Keep one shared backlog where security work ties to the product roadmap.
Run a monthly architecture and tech debt review with security built in to ensure the system is secure by design.
Produce a quarterly, board-ready one-pager (top risks, trends, investment asks).
Define decision rights by category so you don't debate authority mid-crisis.
Document tradeoffs early, because it reduces rework and improves delivery predictability.
Why CISO and CTO relationships break down (and how to name the real problem)
Most breakdowns happen when real work meets real pressure.
A critical feature launch is on the calendar. The team finds a high-risk flaw two days before release. The CTO sees months of effort and a revenue target. The CISO sees customer harm and a headline you can't undo. Both are rational. The conflict is timing, not intent.
Cloud migrations, often central to digital transformation, create the same trap. Engineering wants standard patterns and fast moves. Security wants identity, logging, and data controls to be consistent. If those basics aren't decided early, every workload becomes a one-off argument. That slows everything down.
Vendor onboarding, a key aspect of vendor management, is another repeat offender. Procurement signs, product integrates, then security asks about data flows, breach clauses, and access models. Now you're negotiating under a deadline, with limited leverage, and everyone feels like the other side "showed up late."
Incidents turn minor cracks into open conflict during incident response. A detection gap shows up during an outage. The CTO asks why security didn't catch it sooner. The CISO asks why engineering shipped without basic telemetry. Afterward, the blame game masks the real issue: you never agreed on minimum standards and who decides exceptions.
So what's the real problem? It's unmanaged tradeoffs. When tradeoffs stay implicit, you pay for them later as surprise reviews, emergency fixes, audit scrambles, and "why didn't anyone tell me?" meetings.
If you want a practical frame for executives, think of it like finance versus growth. Neither is the enemy. The enemy is spending without a budget, or growth without unit economics. Security and engineering need the same discipline: clear constraints, clear options, and repeatable decisions.
You are optimizing for different goals, so you need a shared scoreboard
Your CTO is usually judged on delivery, reliability, performance, and cost. Your CISO is judged on risk reduction, control coverage, resilience, and compliance. Those are different lenses on the same business.
The alignment happens when you measure what both sides protect: customer trust, uptime, and revenue. A shared scoreboard prevents the team from "winning" their own metric while the business loses.
A small set of joint metrics works better than a long list. Here are examples you can use without turning this into a reporting circus:
Release predictability (planned vs shipped, and why)
Severity of known vulnerabilities in production (by age and criticality)
Vulnerability management effectiveness (remediation coverage and trends)
Mean time to remediate for high-risk issues (MTTR for security)
Incident containment time (time to detect, time to contain)
Business outcomes protection (customer trust, uptime, revenue trends)
Audit findings trend (open items, aging, repeat findings)
When you review these together, you stop arguing from instinct. You start arguing from impact and trend lines. If you want a deeper executive view on how trust becomes a business outcome, you'll relate to the perspective on https://tysonmartin.com/digital-trust-expert.
Most conflict is really about decision rights and timing
Late security reviews create predictable friction resulting from communication gaps. Engineering feels ambushed. Security feels ignored. Then the organization "fixes" it with more process, which makes everyone slower.
Decision rights solve this, because they remove ambiguity when the pressure is on. A CIO may also be involved in these high-level alignments. You don't need a perfect RACI chart. You need a short map by category, for example:
CTO decides: engineering approach, performance tradeoffs, delivery sequencing within agreed guardrails.
CISO decides: control requirements, risk acceptance thresholds, incident readiness standards.
Joint decisions: launch readiness when risk and delivery collide, new core patterns (identity, logging, secrets), major third-party integrations.
Escalate: stop-ship criteria, material legal exposure, risks that exceed agreed thresholds.
Timing matters just as much as authority. If security only shows up at "release candidate," the only tool left is the brake pedal. If security shows up earlier, you can choose better roads.
The operating rhythm that turns security into delivery flow, not a gate
An operating rhythm is a repeatable cadence with simple inputs and outputs. It's not bureaucracy. It's how you keep decisions small and frequent, instead of big and painful.
Your goal is straightforward: fewer surprises, faster calls, less rework. When you do it well, security starts to look like part of delivery flow, improving secure deployment velocity, because it removes uncertainty.
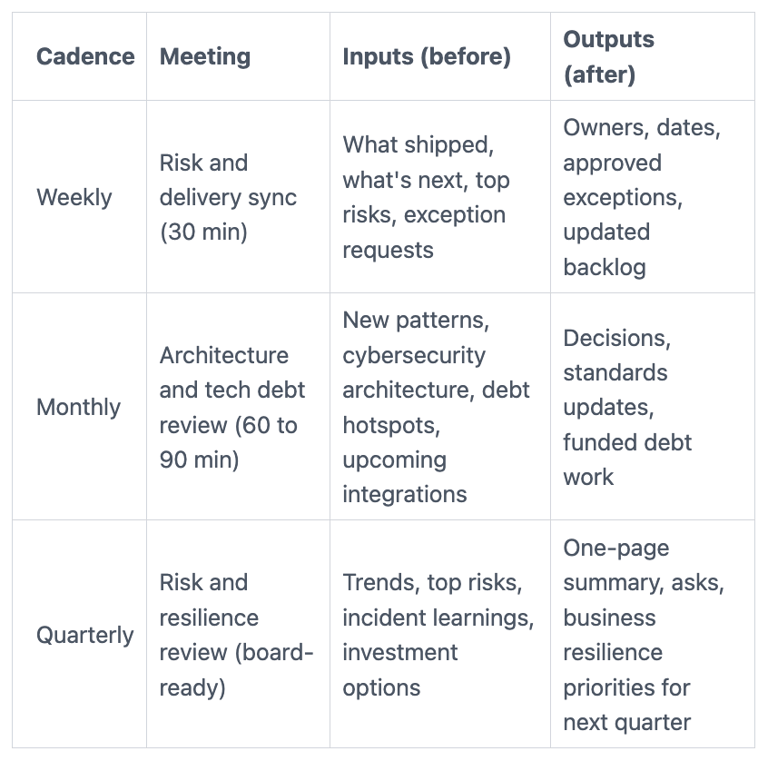
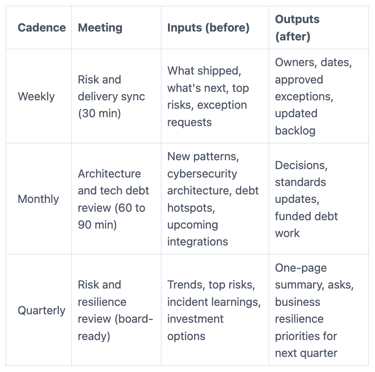
Here's a lightweight cadence you can copy and run with minimal overhead:
This rhythm works best when you treat written artifacts as first-class. If updates only live in someone's head, they vanish when the calendar gets busy.
If it's not written down, it doesn't exist, and you'll argue about it again next week.
If you're building this without a lot of internal capacity, it helps to model it after an advisor-led approach like https://tysonmartin.com/experienced-ciso-for-hire, where the focus stays on decisions and outcomes, not busywork.
Weekly: a 30 minute risk and delivery sync that clears blockers fast
Keep this meeting tight. You're not doing a status parade. You're clearing friction while it's still small.
A simple agenda keeps you honest:
What shipped last week, and what changed in production risk?
What's shipping next, and what decisions are needed now?
Top three risks (not ten), with an owner and a date.
Exceptions requested, with a time box and a mitigation.
Confirm the backlog changes and who updates the notes.
Two rules make this work.
First, run one shared backlog. Security work should not float in a separate universe. Tie it to product epics and reliability work so sequencing stays visible.
Second, keep the attendees small. CTO or delegate, CISO or delegate, the engineering lead for the hottest work, and someone who owns delivery planning. Everyone else can read the notes.
For written updates, ask for four lines per risk: what it is, why it matters, what you're doing, when it closes. That's enough to move fast.
If you want a steady stream of executive-grade patterns for running security in business terms, you can reference https://tysonmartin.com/ciso-insights.
Monthly: architecture and tech debt review, with security built in
Weekly syncs keep you from tripping. Monthly reviews keep you from building the stairs wrong.
This is where you decide on a few "golden paths" and stop re-litigating basics. Focus on the patterns that create repeat risk when they're inconsistent:
Identity and access, secrets handling, logging and monitoring, API standards, data storage, third-party connections, and CI/CD controls.
Instead of asking for a long design doc, ask a handful of questions that force clarity:
What data are you handling, and how sensitive is it?
How do users and services authenticate, and how do you authorize actions?
Where are secrets stored, rotated, and audited?
What must be logged for detection and forensics?
What abuse cases matter (fraud, scraping, privilege misuse), and what's the defense?
Tech debt belongs here too, especially debt that creates operational risk. Old libraries, missing tests, fragile pipelines, and inconsistent telemetry all turn into security problems later. Paying down that debt is how you prevent the "urgent" fire drills that steal whole sprints.
This meeting should end with decisions, not just discussion. If you can't decide, assign a short spike with a deadline. Then decide next month.
Quarterly: a risk and resilience review you can take to the board
Boards don't need a threat feed. They need clarity on material risk, direction of travel, and investment options.
A quarterly one-pager keeps everyone aligned and makes budgeting easier. Keep it plain and tied to business outcomes:
Top risks (three to five), framed as business impact and likelihood
Trend lines on your shared metrics (improving, flat, worsening)
Major initiatives underway (and what they reduce or enable)
Incident learnings (what changed because of them)
Investment asks with options (good, better, best), plus tradeoffs
This is also where you reinforce that "stop ship" is a criteria-based decision, not an emotion-based fight. When the board sees a repeatable method, oversight becomes supportive instead of reactive.
If you're trying to build leaders who can run this rhythm with confidence, ongoing executive growth matters, and the mindset behind https://tysonmartin.com/evolving-and-learning-ciso is a useful model.
Make the cadence stick with clear roles, simple artifacts, and healthy conflict
The hardest part isn't designing the cadence as a formal governance framework. It's keeping it alive when things get busy.
Start by agreeing on what "good conflict" looks like. You want disagreement to show up early, in writing, with options. You don't want it to show up late, in an escalation, with only one painful choice left.
A practical script helps in tense moments: "We're not debating whether this matters. We're choosing when to pay for it, and how we reduce the downside."
Also, keep artifacts lightweight. If they take hours to maintain, they'll rot. If they take minutes, they'll stay current.
Finally, reinforce that security work is real engineering work within DevOps workflows. It needs prioritization, ownership, and deadlines. When you treat it as side work, it becomes last-minute work, and then it becomes emergency work.
If you need to anchor standards and expectations without endless debate, it helps to align to well-known frameworks and qualifications. The overview at https://tysonmartin.com/certified-to-lead shows the kind of standards grounding that makes these conversations easier.
Agree on the "rules of engagement" for exceptions and tradeoffs
Exceptions will happen. The goal isn't zero exceptions. The goal is zero silent exceptions.
A small exception playbook keeps trust intact in the strategic alliance between leaders:
When allowed: a time-bound business reason, not convenience.
What you document: scope, systems, users impacted, time box, and compensating controls.
Who signs: the accountable engineering owner and the security owner, with escalation rules if they disagree.
How it's revisited: a review date in the backlog, not a vague promise.
This removes drama from the moment. You stop arguing about whether you're "allowed" to ship. Instead, you choose the least-bad option and make the cost visible.
Use two shared artifacts: a risk register that engineers will actually read, and a roadmap that shows security work as enablement
Most risk registers fail because they read like audit notes. Make yours readable by engineers and useful for executives.
A simple format is enough: risk statement, impact, likelihood, owner, mitigation, due date, and current status. Keep each risk to two lines. If it needs a page, it's probably three risks.
Your roadmap matters just as much. Show security work as enablement tied to business goals, for example faster onboarding, safer integrations, fewer outages, smoother audits, and faster incident containment, where information security must be seen as an enablement tool. When you connect security work to delivery outcomes, it stops looking like "extra."
FAQs about CISO and CTO relationships and operating rhythm
Who owns the final call when security and delivery disagree?
You avoid most fights by defining decision rights up front. For the remaining hard calls, use an escalation path and require a written tradeoff. True stop-ship should be rare and criteria-based, for example material customer harm, clear legal exposure, regulatory obligations, or inability to detect and respond to likely abuse. When you document the decision, you protect both the CISO and CTO and you keep the board informed.
How do you keep this from becoming more meetings and slower delivery?
You make the cadence replace chaos. A weekly 30-minute sync prevents scattered reviews, surprise escalations, and late rework. Time box it, keep attendees small, and push status into writing. Then use the joint governance monthly review to decide patterns once, instead of debating them in every sprint. This rhythm is essential for managing the technical depth required for modern stacks, including those leveraging artificial intelligence. The result is fewer fire drills and more predictable delivery, not less speed.
Conclusion
You don't have to choose between speed and safety. You can move fast and stay safe when CISO and CTO Relationships run on a simple rhythm, shared metrics, and explicit tradeoffs that satisfy boardroom demands for visibility. The win isn't perfect security or endless caution. The win is fewer surprises, faster decisions, and less rework when it matters most.
This week, set the weekly 30-minute sync, draft decision rights by category, and start a shared backlog for risk and delivery. Next, outline your quarterly one-pager so the board sees trends and options, not noise. When CISOs and CTOs run that operating rhythm, the goal is to protect innovation velocity while maintaining strict security protocols, turning "security vs speed" into one team shipping with confidence.
