Audit Committee Cyber Risk Questions. The Questions That Prevent “We Didn’t Know”
Audit Committee Cyber Risk Questions help you spot weak answers fast, clarify ownership, test controls, and leave meetings with actions, not excuses.


Cybersecurity risk changes faster than most board calendars. Meanwhile, when something goes wrong, the story rarely lands on "attackers are clever." It lands on governance, board oversight, and whether leaders asked the right questions early enough.
That's why "we didn't know" isn't an acceptable outcome for an audit committee. You don't need to become technical, and you don't need to read 40-slide decks; focus instead on board oversight of risk management with questions that force clarity about ownership, funding, readiness, and reporting. When answers are weak, you need crisp follow-ups that turn concern into action.
The Audit Committee Cyber Risk Questions below help you turn cyber from vague fear into clear oversight moves. Think of them like a flashlight in a dark room. You're not trying to run security, you're trying to see what's real, what's assumed, and what's missing.
Key takeaways you can use in your next audit committee meeting
You can separate cybersecurity risk from busy dashboards by asking what's trending and what actions changed it.
You can confirm who owns decisions during incidents, including who can spend money and who can stop operations.
You can spot compliance theater by asking for evidence of internal controls testing, not policy statements.
You can connect cyber oversight to financial reporting and operations by defining "material" in business terms.
You can test third-party risk by requiring inventory by criticality and proof of monitoring.
You can see whether resources match risk by tying budget and staffing to top business risks and security performance outcomes, such as time-to-fix.
You can leave with a short action list (owners, dates, evidence) instead of another "we'll improve" promise.
Start with clarity, what cyber risk means for your business and your audit charter
Cyber oversight works best when you anchor it to business outcomes you already govern: financial reporting integrity, operational uptime amid digital transformation, customer trust, and legal exposure. If your committee charter covers risk management, internal controls, and disclosure, then cyber fits naturally. The trap is treating it as a technical topic, or as a quarterly briefing that never changes decisions.
Start by asking management to frame cyber risk the same way they frame it within enterprise risk management. In other words, "What could happen, how likely is it, how bad would it be, and what are we doing about it?"
Here are practical questions that set that tone, each with what a strong answer sounds like:
How does cyber risk show up in our top enterprise risks? A strong answer links cyber scenarios, including geopolitical risk, to revenue, cost, downtime, safety, and legal outcomes.
Which cyber risks affect financial reporting internal controls? Strong answers connect to systems that feed the general ledger, reporting close, and audit evidence.
What is the audit committee expected to own vs the full board? Strong answers draw a clean line: audit committee focuses on controls, risk process, and reporting; the full board covers strategy, brand, and major risk appetite decisions.
What does "good" look like for this year? Strong answers define 3 to 5 outcomes (for example, reduced time-to-remediate critical issues, tested recovery times, stronger vendor coverage).
Where are we accepting risk on purpose? Strong answers name specific exceptions, owners, and why acceptance makes sense.
Who can explain our cybersecurity posture in plain language to customers and regulators? Strong answers show you've built a repeatable story of assurance, not just a set of tools.
If you want a useful mental model for this, anchor to trust. Customers don't care about your control framework, they care if you keep promises. That's the point of working with a cyber expert like a digital trust expert for board oversight, someone who can translate security posture into confidence, clarity, and priorities.
Questions that define your crown jewels, risk appetite, and what "material" means
When cyber gets fuzzy, it's usually because the business hasn't named its crown jewels and thresholds. You can fix that fast.
What are our crown jewels, the systems and data that would stop the business? A strong answer names a short list, plus dependencies (identity, network, cloud, vendors).
How much downtime is tolerable for each critical service? Strong answers define recovery time and recovery point goals in business language, not vague "ASAP."
What cyber events would trigger a material disclosure or a major customer notice? Strong answers map scenarios to disclosure compliance triggers, decision owners, and timelines.
How do we validate these assumptions? Strong answers reference current impact analysis, real recovery tests, and external benchmarks, not last year's spreadsheet.
Those answers let your committee set expectations: what must be protected first, what must be recovered first, and what must be escalated to the full board.
Questions that make reporting usable with key performance indicators, not a pile of metrics
Dashboards can hide risk when they flood you with activity metrics. You want decision metrics.
What's improving, what's flat, and what's getting worse? Strong answers show trends, with cause and effect.
Which measures predict trouble before it becomes an incident? Strong answers include leading indicators (patch lag on critical assets, untested backups, vendor gaps).
How do you quantify risk in business terms? Strong answers estimate impact ranges, not just counts of vulnerabilities.
What actions did you take, and what did they change? Strong answers connect investment to measurable movement.
Ask for a one-page executive summary plus one page of detail. If management needs 40 slides, they probably don't have a crisp story yet.
If reporting doesn't change decisions, it isn't governance. It's paperwork.
The core Audit Committee Cyber Risk Questions that prevent "we didn't know"
You can keep your cybersecurity risk questions board-level and still be specific. A good set pressures four areas: ownership, controls that matter, incident readiness, and third parties. You're looking for proof of management, not promises.
If you want a steady way to build your committee's muscle over time, keep a small library of board-friendly security explanations and scenarios. Resources like the business side of cybersecurity for executives can help you keep questions sharp without getting pulled into technical weeds.
Ownership and accountability, who is on the hook for results
Who is the single accountable executive for cyber risk, and what's their authority? Strong answers name the chief information security officer or equivalent who can direct priorities and spending.
How do cyber goals show up in executive performance and compensation? Strong answers tie outcomes to incentives (risk reduction, recovery targets, vendor coverage).
How do you prove controls work, not just that they exist? Strong answers cite testing, sampling, and measured security performance.
What is the escalation path to the CEO, audit chair, and full board? Strong answers include triggers, timelines, and who calls whom.
How do internal audit and security coordinate without losing independence? Strong answers show internal audit tests independently, while security fixes and documents.
Where do you have chronic ownership gaps (identity, data governance, cloud, apps)? Strong answers admit gaps and show a plan with named owners and dates.
The signal you want is simple: accountability is explicit, and evidence backs it up.
Controls that matter, are you reducing real risk or just checking boxes?
You don't need to audit every control. You do need to know whether a few high-impact controls are in place and tested.
Which three controls reduce the most risk for us right now? Strong answers prioritize (identity and access, secure change, recovery, monitoring) based on your business.
How quickly do you fix critical issues on crown jewel systems? Strong answers show time-based targets and actual performance.
How do you manage privileged access and admin accounts? Strong answers include least privilege, strong authentication, and regular review.
How do you secure software changes that touch financial reporting or customer data? Strong answers show approvals, testing, and separation of duties.
What is our biggest control weakness today, and what's the plan? Strong answers name one major weakness and a realistic timeline.
Listen for honesty plus focus. If everything is "high priority," nothing is.
Incident readiness, can you make good decisions in the first 60 minutes
Most damage happens during confusion. Your committee can reduce that risk by forcing decision clarity in incident response preparation to build cyber resilience.
Who declares an incident, and who can shut down systems if needed? Strong answers name roles, backups, and authority.
Who speaks to customers, regulators, employees, and investors? Strong answers show coordinated messaging across legal, comms, and exec leadership.
Who decides on ransom payments for ransomware, and what is the policy? Strong answers define decision owners, legal constraints, pre-set criteria (even if the policy is "we don't pay"), and cyber insurance coverage.
How often do you run tabletop exercises with executives, and what changed after the last one? Strong answers show lessons learned that became funded work.
How fast can we restore critical services, and when did we last prove it? Strong answers cite recent restore tests, not just "we have backups."
What did our last incident or near miss teach us? Strong answers focus on root cause, containment time, and control improvements.
In a real incident, you don't rise to the occasion, you fall to your preparation.
Third-party risk and concentration risk, are vendors inside your risk boundary?
A third party with your data is part of your control environment. That includes cloud providers, SaaS tools, payroll, payment processors, and key outsourcers.
Do we have a complete third-party inventory, including supply chain partners, ranked by criticality? Strong answers show a living list, not a procurement export.
What security requirements are mandatory for critical vendors? Strong answers cover access, encryption, incident notice times, audit rights, and subcontractors.
How do we monitor vendors between contract renewals? Strong answers include ongoing signals (attestations, risk monitoring, access reviews).
What happens if a critical vendor fails or is breached? Strong answers include business continuity plans and tested workarounds.
Where are we concentrated (one cloud, one identity provider, one MSP)? Strong answers identify single points of failure and mitigation plans.
How do we handle fourth parties (a vendor's vendor)? Strong answers show contract language and escalation paths.
Turn answers into action, what to request when the answer is weak
Weak answers often sound polite: "We're working on it," "We're advancing our cyber maturity," "We meet the standard." Your job is to provide board oversight by turning that into a short list of requests with owners, dates, and proof.
Here are clean follow-ups that work when you hear uncertainty:
If ownership is unclear, request a 90-day accountability map to advance cyber maturity: one accountable executive, named control owners, and a clear escalation path.
If reporting feels like noise, request a revised cybersecurity risk register for better risk management, in business terms, with a short top-10 list, trend lines, and decisions needed from leadership.
If control claims lack proof, request independent testing (internal audit or an external assessor) focused on a few high-impact controls.
If incident readiness is vague, request an updated incident playbook with decision roles, contact trees, and a schedule for executive tabletops.
If third-party risk is hand-waved, request a critical vendor list and evidence of minimum security requirements and monitoring.
At times, the real issue is capacity, not intent. When risk outgrows the team, consider strategic cybersecurity leadership for audit committees to stabilize execution, improve reporting, and drive closure on the hard items.
To track progress without drama, use a simple red, yellow, green view.
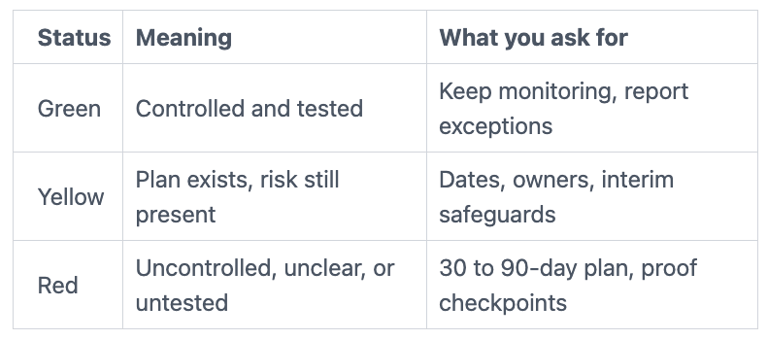
A simple follow up pack you can ask for by next meeting
Ask management for a tight packet you can read in 20 minutes:
Top cyber risks (top 5 to 10), each with an owner, impact, and next milestone
Penetration test or independent assessment summary, plus what got fixed and what didn't
Critical third-party list ranked by business impact, with current assurance status
Incident roles and call tree, including after-hours coverage and decision authority
Backup and restore test results for crown jewel systems, with actual recovery times
Awareness and phishing trends, focused on outcomes (reporting rates, repeat offenders)
Budget vs plan, with implications for financial reporting, tied to the top risks and the year's expected outcomes
Exceptions and accepted risks, including who approved them and expiry dates
FAQs boards ask about cyber oversight and audit committee responsibility
How often should cyber be on the agenda? Put it on the agenda at least quarterly, with attention to regulatory trends, and more often after major change or incidents.
What evidence is "enough" for oversight? Look for proof of testing, trends over time, and closure on findings, not just policies.
What if management can't quantify risk? Start with ranges and scenarios tied to downtime, revenue loss, and disclosure compliance triggers, then improve precision.
How should you handle cloud and third-party risk? Treat key vendors as part of your control environment, require inventory by criticality, and demand ongoing monitoring.
What should you expect from internal audit? Internal audit should test the design and effectiveness of risk management controls independently, then track remediation to closure.
What do you do after a near miss? Ask for a root-cause summary, what changed, and what would have prevented it completely.
How do you avoid metric overload? Require one page of plain language and only metrics that drive decisions. For broader board readiness, continuous learning matters, and a perspective like continuous learning in cyber oversight leadership helps keep questions grounded and current.
Conclusion
You're not trying to run security from the audit committee. You're making sure management can prove readiness, reduce business risk, and report security performance in a way that supports decisions. The fastest way to raise confidence is to pick 10 questions from this list for your next meeting, set expectations for evidence, and track actions, including vulnerabilities, to closure.
When you keep the focus on ownership, tested controls, incident decisions, and third parties to build cyber resilience, "we didn't know" becomes much harder to say. If you want support turning these questions into a steady governance cadence, trusted leadership matters, and certified strategies for audit committee cybersecurity risk can help you set clear standards without slowing the business down.
