Best Cybersecurity Board Advisor. The Mistakes Boards Make When They Choose One
Choose the Best Cybersecurity Board Advisor by avoiding common board mistakes, getting 10-minute briefings, decision-ready metrics, and incident practice.


You probably don't have a board of directors that "ignores cyber." Most boards care, ask questions, and approve budgets. Still, breaches keep happening, and directors still get surprised.
The usual failure isn't apathy. It's choosing the wrong kind of cyber risk management help, then asking for the wrong outputs. A board hires a cybersecurity board advisor expecting calm, clear guidance. Instead, it gets dense slide decks, tool debates, or compliance theater that looks good until a real incident hits.
A cybersecurity board advisor isn't a hands-on SOC operator, and they shouldn't try to be. Their job is to strengthen governance, sharpen oversight, and help you evaluate your information security posture to make business decisions with your eyes open. That means translating cyber risk into choices you can approve, fund, measure, and revisit.
In the next few minutes, you'll get a simple way to spot common selection mistakes and choose an advisor who can brief your board like an executive, not like a vendor.
Key takeaways you can use before you hire a Cybersecurity Board Advisor
Ask them to brief your board in 10 minutes, with a one-page summary you can reuse.
Require decision outputs, not "board-level awareness," for example approve, defer, accept, or fund.
Insist on measurable outcomes, such as reduced exposure, faster containment, or clearer ownership.
Avoid compliance-only advisors focused on regulatory compliance who can't explain how an attack would actually unfold.
Test independence, ask how they handle bad news and pushback from management.
Demand a plan for incident readiness through incident response planning, including a tabletop and a weekend escalation path.
Confirm they can coach the CEO and GC in working with the CISO, not just talk to IT.
Define scope in writing, so they don't drift into tool selection or daily operations.
What the best cybersecurity board advisor actually does for you
A Best Cybersecurity Board Advisor delivers Strategic Oversight that makes your oversight easier, not heavier. You get fewer surprises, clearer tradeoffs, and faster decisions when time matters. They help you set a standard for what "good" looks like, then keep the organization moving toward it.
A Cybersecurity Board Advisor's value shows up in four places.
First, they help you govern Cyber Risk Management with a shared language. Without that, every update becomes a debate about technical detail. With it, your board can agree on risk tolerance, priorities, and timing.
Second, they create board-ready reporting on Cyber Risk Management that tells the truth. You see top risks, trends, exposure, and whether management is doing the hard work. You also see what's stuck and why.
Third, they raise your Cyber Resilience for incidents. When a breach hits, you don't want to improvise roles, messaging, and authority. You want muscle memory. A strong advisor helps you rehearse the board's role, including legal, comms, and customer impact on Business Continuity.
Fourth, they help protect trust. Customers, regulators, partners, insurers, and Cyber Insurance Policy providers react to how you govern and respond, not just what tools you own. That's why many boards look for someone who thinks like a trust leader, not a "security-only" specialist. You can see that lens in a Digital Trust Expert for boards who frames security as confidence, accountability, and proof.
If you want examples of how this looks in practice, you can also scan CISO insights for executives to compare your current approach to a more board-focused one.
The advisor's job isn't to run security for you. It's to help you run oversight like you mean it.
They turn technical risk into business choices the board can act on
A strong advisor doesn't lead with fear. They lead with clarity.
You should expect them to express risk in the currencies your board already uses: money, uptime, safety, legal exposure, and brand trust. That translation changes the conversation. Instead of "Are we secure?" you get "Which risk are we accepting, and why?"
For example, they help you make board-level Risk Mitigation decisions like:
Accepting a known risk for 6 months to hit a revenue deadline, with compensating controls.
Funding identity improvements because the current risk ties to fraud loss and outage risk.
Resetting a timeline because a third-party dependency creates a single point of failure.
Approving a phased plan because the org can't absorb 12 major changes at once.
Just as important, a good advisor explains tradeoffs without hiding the downside for effective Risk Mitigation. You get options, assumptions, and what changes the recommendation.
They help you build a simple oversight rhythm, not a pile of slides
Boards don't need more content. You need a rhythm that creates pressure and visibility.
A practical cadence is simple: quarterly board updates, monthly committee touchpoints, and fast escalation when something breaks. Reporting should stay consistent, so trends stand out.
Good reporting usually covers:
Top enterprise cyber risks (ranked, with owners and timelines)
Control maturity (where you're improving, where you're stalled)
Incident readiness (playbooks, exercises, decision authority)
Third-Party Risk (critical vendors, concentration risk, assurance gaps)
You should avoid reporting that turns into tool inventories, "patch counts" without context, or vanity metrics that always look green. If your dashboard can't drive a decision, it's noise.
The biggest mistakes boards make when choosing a cybersecurity board advisor
You can do everything "right" on paper and still end up with weak oversight from a Cybersecurity Board Advisor. These are the mistakes that create false confidence and slow you down when it matters.
Mistake 1: Hiring someone who can talk for an hour, but not for ten minutes.
Board time is scarce. If the advisor can't land the point fast, you'll drown in detail. The downside is predictable: directors tune out, and risk decisions drift.
Mistake 2: Treating the role like a one-time assessment.
A point-in-time review can help, but governance needs continuity. Without it, you get a nice report, then regression. Attackers don't care that you were "reviewed" last spring.
Mistake 3: Confusing "framework fluent" with "board effective."
Frameworks matter, but they're not the outcome. If the advisor can't connect the NIST Cybersecurity Framework, SEC Cybersecurity Rules, or ISO to your strategy, budget, and operating model, you'll buy paperwork instead of progress.
Mistake 4: Hiring an advisor who can't challenge management.
Your advisor should be respectful, but firm. If they avoid tension, bad news gets softened. During ransomware attacks, that habit turns into delayed escalation.
Mistake 5: Letting the advisor drift into tool selection and operations.
Boards hire advisors for cybersecurity governance. When the work becomes tool shopping, you lose independence and waste time. The CISO and team should run day-to-day execution. The board should govern priorities and outcomes.
Mistake 6: Overvaluing brand names and undervaluing judgment.
A famous logo doesn't guarantee good board counsel from a cybersecurity strategist. What matters is how they think under pressure, how they handle ambiguity, and whether they can align people who disagree.
Mistake 7: Ignoring how the advisor stays current.
The threat landscape, regulation, and business tech change fast. An advisor who learns in public, tests ideas, and updates their thinking will serve you better than someone stuck in old patterns. Look for evidence of ongoing growth, like an evolving CISO with continuous learning.
Mistake 8: Treating credentials as the whole evaluation.
Certifications can signal discipline, but they don't prove boardroom skill. Use credentials as a filter, not a finish line. When relevant, they do help you trust baseline competence, such as a certified CISSP and CISM leader who has proven governance and risk grounding.
Mistaking a great operator or auditor for a board-ready advisor
A great operator can build and run security programs. A great auditor can test controls and compliance. Neither automatically translates to board advisory.
The gap is governance. A board advisor has to define decision points, set an oversight cadence, and speak in outcomes. Some operators struggle to simplify. Some auditors focus on evidence and checklists, then miss real attack paths and business continuity gaps.
You don't want an advisor who only says, "You're not compliant." You want one who can say, "Here's how you could get hit, here's what breaks, here's what it costs, and here are your options."
Hiring for buzzwords instead of decision support
Buzzwords are easy to buy. Decision support is harder.
You'll hear AI, zero trust, and every new acronym. None of that matters if the advisor can't help you choose priorities, sequences, and tradeoffs.
Use a simple test in interviews: ask them to explain your top cyber risk in 60 seconds, then propose three board actions. If they can't do that cleanly, the work will turn into jargon and slide weight.
How you evaluate and choose the right advisor, step by step
You'll get better results if you treat selection of a Cybersecurity Board Advisor like you would any executive hire, mindful of your Fiduciary Responsibility. Start by writing the outcomes you want, then measure candidates against them.
Begin with scope. Decide whether you need independent board oversight support, Independent Cyber Risk Review, incident readiness, reporting redesign, or all three. Next, confirm how the advisor will interact with the Executive Leadership Team (CEO, CISO, GC), and the Audit Committee or risk committee. A good advisor strengthens the CISO's position while still giving the Board of Directors independent clarity.
Then ask for proof. You want examples of board updates, metrics, and incident exercises. You also want stories of disagreement, because that's where judgment shows up.
Finally, set the operating rhythm up front. Define meeting cadence, what "good" reporting looks like, and what decisions the advisor will tee up for the board.
If you're comparing profiles, it can help to look at what "board-to-breach" experience looks like for a Board Ready CISO in an Experienced CISO for Hire, then map that experience to your needs. When you're ready to formalize the relationship, use a clear engagement path, such as engage a CISO advisor, so expectations don't get fuzzy.
Use a short scorecard to compare candidates the same way
A scorecard keeps you from hiring the best talker instead of a true Trusted Advisor. Use a 1 to 5 scale, add a red-flag column, and have the committee fill it out separately.
Here's a simple structure you can copy into your process:
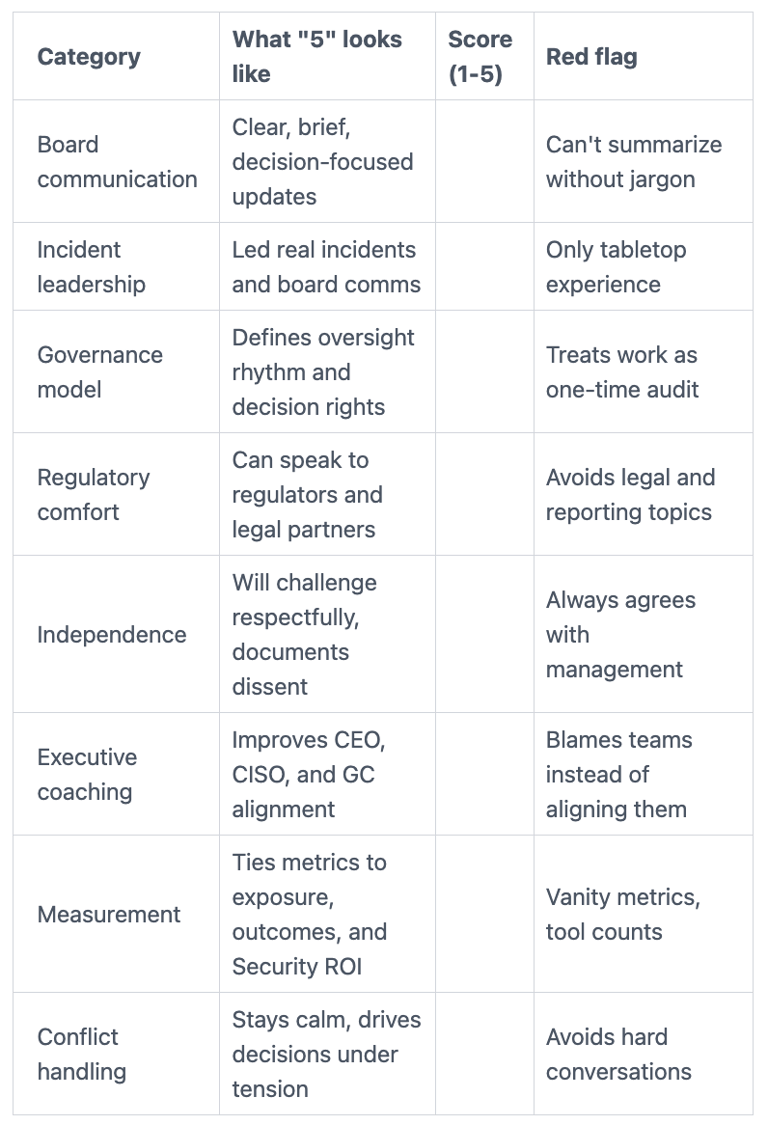
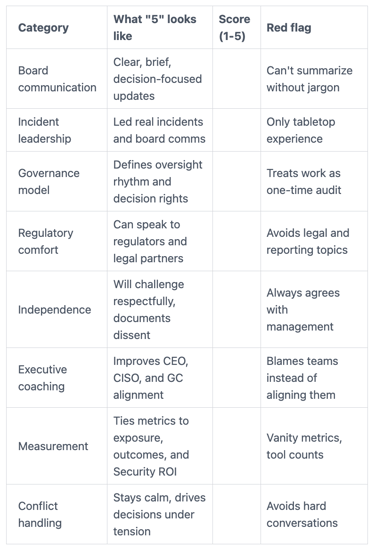
The takeaway is simple: you're scoring judgment and clarity, not technical trivia.
Ask interview questions that reveal judgment under pressure
These questions push past rehearsed answers:
"Walk me through your first 30 days with our board."
"Show me a one-page board cyber update you'd use."
"What are the three metrics you'd want from management, and why?"
"Tell me about a time you disagreed with a CEO." (Strong answer: names the risk, the tradeoff, and the final decision.)
"How do you handle a breach on a weekend?" (Strong answer: clear escalation, roles, and communication guardrails.)
"What do you do if management hides bad news?"
"How do you avoid turning board reporting into compliance theater?"
"Where do you draw the line between governance support and operational work?"
"How do you assess third-party risk without drowning in questionnaires?"
"What would make you resign from an advisory role?"
You're listening for calm, direct language, and a bias toward decisions.
FAQs boards ask about hiring the best cybersecurity board advisor
Do you need a cybersecurity board advisor if you already have a CISO?
Yes, often you do. Your CISO runs the program and reports up through management. An advisor can support independent oversight and cybersecurity governance, improve board reporting, and rehearse crisis decision-making without undercutting management. In addition, a good advisor can coach both sides so the board gets clarity and executives get air cover.
What should you expect in the first 90 days?
Expect a fast intake of business context, current risks, and your "crown jewels." Next, the advisor should review your security program and critical vendors at a high level, then baseline your information security posture and board reporting so you can track trends. You should also run an incident tabletop with executives and board leaders to strengthen cyber resilience. By day 90, you want a prioritized roadmap the board can approve, with owners and milestones.
Conclusion
When you hire a Cybersecurity Board Advisor, you're investing in core pillars like Regulatory Compliance and Incident Response Planning. You're not buying more documents. You're buying better decisions, clearer oversight, and a calmer response when pressure spikes, especially in technical areas like Material Incident Disclosure and Vulnerability Management.
If you remember one thing, make it this: the Board of Directors don't fail because they didn't care. They fail because they hired help that couldn't translate Cyber Risk Management into action. Avoid the common traps, especially buzzword hiring around Phishing Simulation Metrics in isolation, compliance-only thinking, and advisors who won't challenge management.
Use the scorecard, run the pressure questions, align on outcomes and cadence with your CISO and Trusted Advisor as the Cybersecurity Strategist for Risk Mitigation before you sign. Your next incident won't wait for a better process, so choose clarity now.
