Best Interim CISO: The 10 Traits That Separate Stabilizers From Talkers
Hire the Best Interim CISO by spotting week-one proof: 30-day plan, top risks, incident readiness, board-ready updates, clean handoff in 2 weeks.


When a breach hits, an audit slips, or your Chief Information Security Officer walks out, you don't need a big speech. You need cybersecurity leadership, fast. You also need progress you can point to without spinning a story.
That's what the best interim CISO means here: someone who steps in during the transition period, gets the facts, calms the room, and makes risk easier to manage within days, not quarters. They earn trust across IT, legal, finance, and product, because they don't guess. They confirm. They don't flood you with meetings. They create an operating rhythm that reduces surprises.
Most importantly, they leave you stronger than they found you. Not with a binder, but with a clearer risk picture, better incident readiness, and a plan your team can execute after they're gone.
Key takeaways: how to spot the best interim CISO fast
In the first two weeks, you can verify real capability. Look for proof like this:
A clear 30-day plan assessing security posture with week one actions, owners, and decisions needed from you.
A ranked top-10 risk list informed by vulnerability assessment and tied to business impact from cyber threats, not a gap analysis of tool gaps.
An incident readiness check that confirms contacts, authority, comms paths, and evidence handling.
A quick access and privilege review focused on the accounts that can hurt you most.
Backup and recovery validation (what's protected, what's tested, what actually restores).
A simple reporting cadence (weekly exec update, monthly board summary, no jargon).
Fewer "unknowns" every week, because asset ownership and accountability get clarified early.
Two to three quick wins that reduce real risk without slowing teams down.
If you can't see these outputs quickly, you're watching activity, not stabilization.
What "best interim CISO" really looks like in the first 30 days
An interim leader can stay busy and still fail you. Activity looks like workshops, new slide decks on cybersecurity strategy, and a long list of "next steps." Outcomes look like fewer open questions, tighter control of critical systems, and decisions you can make with confidence.
A realistic 30-day arc for an interim CISO or Virtual CISO is simple and repeatable. First, they listen. They meet the people who run identity, endpoints, cloud, apps amid digital transformation, and third-party risk management. Next, they triage risk. That means turning scattered concerns into a short ranked list with plain reasons. Then they stabilize the basics that fend off cyber threats and keep you up at night: access, logging, backups, incident paths, and change control on critical systems.
By the end of the month, you should have a short execution plan outlining the information security strategy for the next 60 to 90 days. It shouldn't read like a wish list. It should read like a work order.
If the interim CISO can't explain "what changes next week" in five minutes, you don't have momentum. You have noise.
The stabilizer playbook: regain control without slowing the business
A stabilizer starts with facts, not opinions. They confirm who owns what, then they fix the gaps that create chaos during incidents. They tighten change control where it matters most, without turning every release into a courtroom.
They also validate what's real. Backups that haven't been tested are hope, not recovery. Logs that nobody reviews won't help during a breach. Escalation paths that depend on one person won't work at 2 AM.
Finally, they pick a few quick wins that reduce risk quickly. Think: MFA on key admin paths, removing stale privileged accounts, shoring up endpoint visibility, or hardening your most sensitive SaaS settings. You'll feel the difference because leaders get fewer "urgent" surprises.
What talkers do instead (and why it wastes your time)
Talkers start by rewriting your strategy before they understand your reality. They over-promise timelines. They blame the past. They create new committees. Meanwhile, basics stay shaky.
You'll also see them skip the uncomfortable work: asset ownership, access reviews, incident communications, and recovery testing. Instead, success becomes "meetings held" or "roadmap delivered."
That approach costs you twice. First, risk stays high. Second, your team loses trust because they see theater instead of help.
The 10 traits that separate stabilizers from talkers
Below are the traits you can look for, even if you aren't a security expert. For each one, focus on what you can see in week one, how you verify it, and the red flags that signal talk without traction.
Trait 1 to 5: you get calm leadership, clear priorities, and fast traction
Trait 1: Calm under pressure
What it is: Steady incident leadership with clear decisions.
Week one: They confirm who declares an incident and who can take systems offline.
Verify it: Ask for the incident decision tree and first draft comms plan.
Red flags: Drama, urgency without direction, or "we need more data" as a stall.
Trait 2: Rapid risk triage
What it is: Risk management that turns scattered issues into a ranked list you can act on.
Week one: You get a top-10 risk list with business impact and confidence level.
Verify it: Ask why risk #3 is above risk #7, in plain terms.
Red flags: Everything is "critical," or priorities change every meeting.
Trait 3: Business-first communication
What it is: Plain language tied to revenue, mission, safety, and uptime.
Week one: Updates focus on decisions and trade-offs, not tool features.
Verify it: Drop them into an exec meeting and see if people leave aligned.
Red flags: Fear tactics, jargon, or "because compliance" without context.
Trait 4: Tight execution discipline
What it is: Owners, dates, and a lightweight operating rhythm.
Week one: A short backlog appears, each item has an owner and due date.
Verify it: Spot-check three items, ask owners what "done" means.
Red flags: No dates, no owners, or endless "alignment" sessions.
Trait 5: Builds trust across teams
What it is: Cross-functional follow-through, fewer surprises, cleaner handoffs.
Week one: They meet the Chief Information Officer, product, legal, HR, and finance, then map shared risks.
Verify it: Ask those leaders if they feel helped, not judged.
Red flags: Us-versus-them language, or constant escalation without coaching.
If you need stabilization fast and you want a leader who can step in cleanly, it helps to engage a CISO advisor for rapid stabilization instead of waiting for a long hiring cycle.
Trait 6 to 10: you get governance, resilience, and a clean handoff
Trait 6: Incident-ready mindset
What it is: Incident response preparedness that holds up under stress.
Week one: They run a short tabletop on a likely scenario.
Verify it: Confirm evidence handling, decision authority, and external contacts.
Red flags: "We'll build the plan later," or unclear legal and comms involvement.
Trait 7: Standards fluent, not standards obsessed
What it is: Ability to map to NIST or ISO for regulatory compliance without boiling the ocean.
Week one: They align priorities to a simple framework view, then move to actions.
Verify it: Ask which controls matter most for your current risks.
Red flags: A compliance rewrite before fixing known exposure.
Trait 8: Controls that fit the business
What it is: Policies and controls people will follow.
Week one: They remove friction in one high-pain workflow (for example, access requests).
Verify it: Check adoption signals, fewer workarounds, faster cycle times.
Red flags: Heavy policy dumps, or "security says no" as the default.
Trait 9: Board and executive reporting
What it is: Simple metrics, trends, and decisions needed.
Week one: You get a one-page risk snapshot with current posture and movement.
Verify it: Share it with a board member, ask if it's clear in two minutes.
Red flags: Vanity metrics, or a 30-slide deck to explain one risk.
Trait 10: Leaves you stronger than they found you
What it is: Real capability uplift in security governance, not dependency on the interim leader.
Week one: They identify who will own each capability when they exit.
Verify it: Ask for the handoff plan outline on day 10, not day 80.
Red flags: Knowledge hoarding, or a plan only they can run.
When these traits show up together, you get more than "better security." You build the kind of customer and board confidence that comes from digital trust outcomes leaders can feel.
How to evaluate an interim CISO before you hire (and in the first two weeks)
You're not buying a title. You're buying time, clarity, and reduced risk. Unlike working with an executive search firm for a permanent hire, which often involves accessing passive talent pools and takes months, an interim CISO delivers speed. So evaluate an interim CISO the same way you'd evaluate an emergency contractor. Can they show up, diagnose fast, and fix what matters first?
Before you hire, ask for artifacts, not promises, as part of the CISO recruitment process. In the first two weeks, judge them by deliverables and the team's response. You should see calmer operations, fewer unknowns, and faster decisions.
A simple scorecard keeps you honest. Rate each category 1 to 5, then review it at day 14.
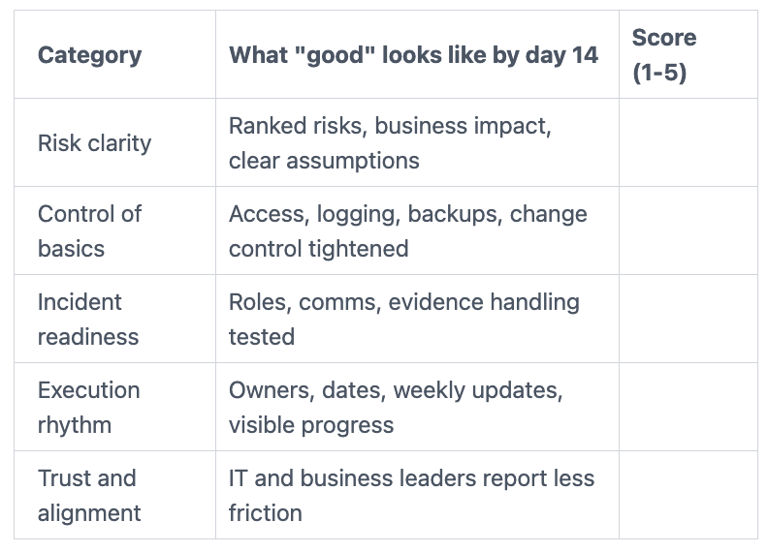
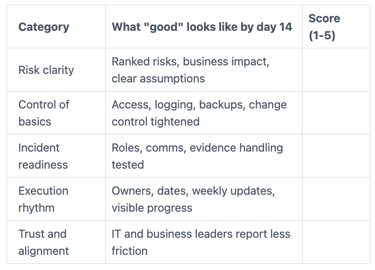
If they score well, you'll feel steadier even before the big fixes land.
Interview questions that force real answers
Use questions that require specifics, not philosophy:
Show me your 30-day plan template. What do you change for my org?
Tell me about a time you stopped the bleeding in week one. What did you do first?
How do you handle a breach with limited facts in the first two hours?
What authority do you need from me as CEO on day one as Chief Information Security Officer?
How do you work with a Chief Technology Officer when priorities conflict?
Show an example of board reporting that led to a decision.
Which controls do you verify first, and why?
What do you always leave behind when you exit?
If credibility matters in your environment, ask how their training and credentials, including CISSP certification, support executive leadership expectations, then review a track record like certified CISO leadership credentials alongside real examples.
Week one and week two deliverables you should expect
By the end of week two, you should have a small set of documents and actions you can use immediately:
Current-state snapshot (what's known, unknown, and assumed)
Top risks with rationale (not just vulnerabilities)
Immediate actions taken (what changed, where, and why)
Incident readiness gaps and next actions
30 to 90-day security roadmap with owners and dates
Stakeholder map (who must be in the room for key decisions)
A simple cadence for exec updates and board summaries
If you want a reference point for what strong CISO operating rhythms look like, you can compare notes with practical CISO insights on execution and oversight.
FAQs about choosing the best interim CISO
Cost, timing, authority, and outcomes: the questions leaders ask most
How long should an interim CISO stay?
CISO tenure is often 3 to 9 months. You want enough time to stabilize and set a plan, not enough time to become a permanent crutch.
Interim vs fractional vs full-time, what's the difference?
Interim usually means high-intensity, near-term leadership. Fractional CISO services provide part-time coverage over a longer period. Full-time is the long-term owner.
What authority do you need to give them?
They need clear decision rights for incident response, access changes, and risk escalation. Without that, they can only advise, not stabilize.
How do you measure success?
Look for reduced uncertainty, fewer high-risk gaps that drive up data breach cost, improved incident readiness, and a credible 60 to 90-day plan that's already moving.
Can an interim CISO lead incident response?
Yes, if they've done it under pressure. Ask for examples of containment decisions, comms coordination, and recovery validation ensuring business continuity.
How do they work with MSPs and internal IT?
They should clarify ownership, set expectations, and reduce churn. If the MSP provides managed security services and runs security tools, the interim CISO should still own risk decisions.
When should you bring in an experienced interim leader?
Bring one in when you have a live incident, a failed audit, a leadership gap, or a board that needs clearer oversight. In those cases, hiring an experienced CISO for hire, such as a virtual Chief Information Security Officer, can be faster than rebuilding confidence through trial and error.
Image brief: photo-realistic editorial image for this article
Photo-realistic editorial photograph, calm, focused, resilient, trustworthy, human, practical mood. Over-the-shoulder view of a small leadership team (3 to 4 people) collaborating at a clean conference table, reviewing a printed incident response plan and a risk dashboard on a laptop (screen blurred beyond legibility). Hands visible with pens and a notebook, one person pointing at a section of the printed plan turned slightly away so no words are readable. Soft natural light from a window, gentle contrast, premium and uncluttered composition. Color grading with deep navy and slate undertones, subtle coastal blue or spruce green accents, warm gold highlights, and light sand or off-white neutrals. Shallow depth of field, 25 to 35 percent negative space on one side for blog layout. Background includes a whiteboard with simple shapes and lines conceptually representing cybersecurity strategy and risk management (no readable writing) and a few sticky notes blurred beyond legibility. No logos, no text, no readable documents, no readable screens.
text, words, letters, numbers, typography, captions, labels, signage, watermarks, logos, brands, readable screens, readable documents, interface mockups, QR codes, banners, headlines, icons with letters, distorted text
Conclusion
A strong interim CISO doesn't win by talking louder. They win by making risk management visible, decisions easier, and operations steadier. When you hire the Best Interim CISO, you're buying calm leadership, fast triage, clear communication, disciplined execution, cross-team trust, incident readiness, practical standards alignment for regulatory compliance, right-sized controls, board-ready reporting, a robust cybersecurity strategy, and a clean handoff.
Use the checklist above, then insist on week one proof. You should see fewer unknowns, tighter control of the basics, and a plan that's already moving. If you're building your own leadership habits as a Chief Information Officer or Chief Technology Officer along the way, keep investing in the mindset behind strong execution and information security strategy, including continuous growth as a security leader.
