Board Cyber Risk Advisor. The Fastest Way to Clarify Risk Appetite and Escalation
Board Cyber Risk Advisor helps you set clear risk appetite and escalation in weeks, so your board makes faster calls, with fewer surprises.


If your Board of Directors only talks about cyber risk when something goes wrong, you're not alone. Most boards don't lack concern, they lack a shared definition of cyber risk management and cyber risk oversight, what's acceptable and what requires immediate attention. When risk appetite is fuzzy, every incident feels like a surprise. When escalation is inconsistent, decisions arrive late, or arrive in a panic.
A Board Cyber Risk Advisor helps you fix that gap fast. You get a bridge for strategic oversight between the board, the CEO, and security leadership, with one job: turn cyber risk into clear decisions, clear thresholds, and clear ownership. You're not signing up for a long program review that takes quarters. You're setting the tone at the top on the few choices that prevent confusion, usually in weeks.
The outcome is simple: fewer surprises, faster decisions, clearer accountability, and reduced business impact.
Key takeaways you can use in your next board meeting
These actionable insights support corporate governance by guiding board oversight of cyber risks.
In risk management, cyber risk appetite means the board agrees on what "not ok" looks like in business impact terms.
You only need a few inputs to start, your crown jewels, top obligations, and recent incidents, to shape your cybersecurity strategy.
In cybersecurity governance, a one-page appetite statement reduces "we need more data" debates.
A one-page escalation ladder prevents both silence and overreaction.
The board owns thresholds and risk acceptance for material issues, management owns execution.
Your incident updates should follow pre-set triggers, not whoever is loudest in the room.
Next week, run one workshop to draft appetite and escalation, then test it in a tabletop followed by cybersecurity awareness training.
What a Board Cyber Risk Advisor actually does (and what you should expect in the first 30 days)
A Board Cyber Risk Advisor, serving as a cybersecurity advisor, is not there to run your security tools or rewrite your policies. You bring them in to make cybersecurity governance work under pressure. In plain terms, they help you agree on what matters most, how much disruption you can tolerate, and when the board must get pulled in.
That role differs from other common support:
A CISO runs the day-to-day security program, leads the team, and delivers outcomes over time.
A consultant often focuses on projects, assessments, or implementations.
An auditor tests against a standard and reports gaps.
An advisor provides independent cyber risk reviews, sitting in the middle and translating information security reality, without technical jargon, into board decision language. You should expect early focus on your business model, critical services, and "decision friction." That friction shows up when everyone sees risk, but nobody knows who decides, by when, and based on what threshold.
In the first 30 days, you're usually working toward two fast deliverables: a one-page risk appetite statement and a one-page escalation ladder (more on those below). Along the way, you'll also tighten meeting routines, improve how updates are written, and perform a materiality analysis for your organization, not for a generic template.
You typically need this help when your board is new to cyber oversight, your company is growing fast, you've had a recent material incident, regulators are asking tougher questions on SEC cybersecurity rules, you're doing M&A, or security leadership is turning over. Those moments create a nasty mix of urgency and uncertainty, so clarity becomes a safety feature.
Your board is not asking for more data, it is asking for clearer decisions
Many boards already get dashboards. The problem is that dashboards often arrive without decision thresholds. As a result, everything looks "high," and nothing feels actionable to fulfill fiduciary responsibility.
Here's what usually breaks:
Poor escalation often hides behind busy reporting. You see weekly risk registers with no "trigger lines." You get incident updates that land after key containment choices are already made. Meanwhile, risk acceptance happens in an email thread, with no record of who owned the call. Ownership also blurs when IT, security, legal, and business leaders assume someone else is deciding.
A better approach is to frame cyber risk so the board can decide. For example, when risk is stated as, "This customer portal could be down for 24 hours during peak season due to a single point of failure," the board can respond with a real choice: approve funding, delay a launch, require a control by a date, or accept the risk with eyes open.
If you can't point to the decision you want, your report is not board-ready.
The fastest deliverables that create clarity, a one-page appetite statement and a one-page escalation ladder
These two pages work like guardrails on a mountain road. They don't drive the car for you, but they keep you out of the ditch.
Your one-page appetite statement puts cyber risk into a short set of business tradeoffs. It spells out what you protect first, what kinds of impact you won't accept, and where you're willing to take calculated risk to hit growth goals. It also defines "material" in your terms, usually anchored to money, downtime, customer harm, and legal duty.
Your one-page escalation ladder answers, "When does this move from management to executives to the board?" It defines triggers, who notifies whom, expected response time, and what information must be included in the first update.
Together, these pages reduce debate because they replace opinions with agreed thresholds. They're also living documents. As your products, revenue, and obligations change, you adjust the thresholds. The format stays stable, so decisions stay calm.
Clarify cyber risk appetite in one workshop by making tradeoffs visible
If you want speed, you need structure. A practical workshop turns "we should be secure" into "we choose these priorities, and we accept these tradeoffs." With a Board Cyber Risk Advisor, you can often draft appetite in one working session, then refine it with follow-ups. Keep discussions free of technical jargon to ensure everyone stays aligned.
A simple workshop flow looks like this:
Conduct a risk assessment to agree on your crown jewels and the impact types that matter most.
Pick the time horizon for decisions (this quarter, next year, three years).
Define what "not ok" means using clear thresholds.
Confirm what the board owns vs what management owns.
Write the one-page appetite statement, then assign an owner to keep it current.
This is also where "trust" becomes practical. You're not chasing a vague goal. You're making explicit promises to customers, regulators, and partners about your regulatory compliance in protecting operations and data. If you want a board-level view of that trust-building approach, the framing in digital trust guidance for CEOs and boards aligns well with this workshop style.
Start with what you are protecting, money, operations, customer trust, and legal duty
Start by naming what you can't afford to lose. Think of it like a fire drill. You don't begin by debating the best hose. You begin by asking what must get out of the building first.
Your "crown jewels" might include revenue systems (checkout, billing), operational systems (manufacturing, logistics), sensitive data (customer PII, health data, payment data), or safety-related systems. These are assets you must protect from cyber threats. Then map those jewels to impact types: financial impact, downtime, privacy harm, regulatory penalties, and reputational damage.
An advisor will push you to choose priorities for cyber risk management and time horizons. For example, you might tolerate more disruption in an internal system this quarter if it protects a customer-facing launch. On the other hand, you might decide that regulated data exposure is never acceptable, even if it slows growth. Those choices are uncomfortable, which is why they work. They surface the real appetite that was already there, just unstated.
Turn opinions into thresholds, define what "not ok" looks like
Once you name what matters, you turn opinions into thresholds that define risk tolerance, lines in the sand for what "not ok" looks like including financial loss. The examples below are generic, so you must tailor them. Still, they show the style that boards can approve and management can execute, all in plain business terms without technical jargon.
Here are example threshold statements, expressed in plain business terms:
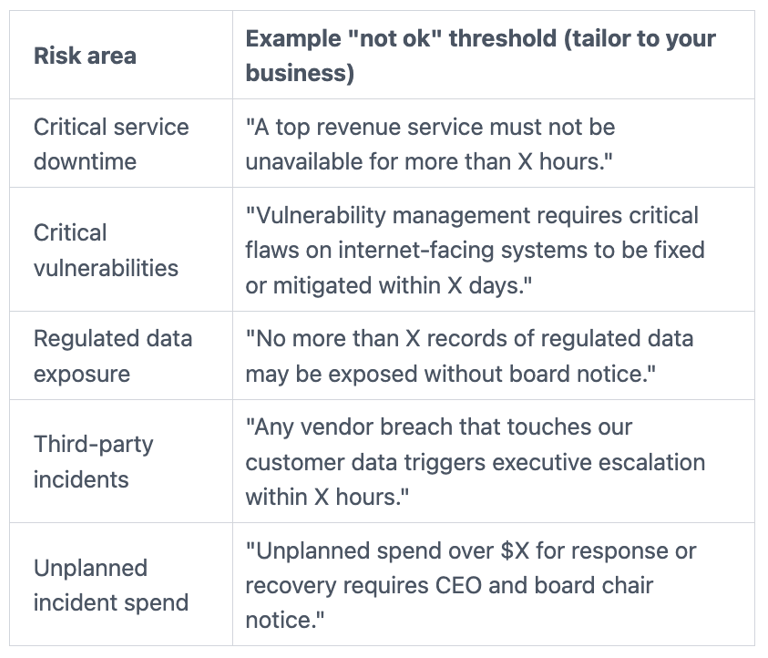
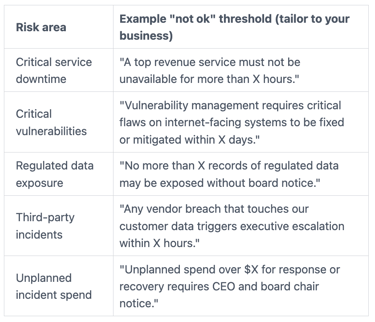
Frameworks like NIST or ISO can help management map thresholds to controls, audits, and plans. These thresholds reflect your organization's information security posture. However, you don't need a heavy framework conversation in the boardroom. You need agreement on impact, thresholds, and accountability.
Build an escalation path that prevents surprises and avoids panic
Escalation isn't a reporting habit. It's a decision system. When you treat it that way, your teams stop guessing, and your board stops feeling blindsided.
A cybersecurity advisor helps you define triggers that match your appetite statement. Then you attach each trigger to a response level in your Incident Response Plan, a notification list, and a required update format. This makes escalation predictable, which builds cyber resilience and keeps people calm when pressure spikes.
This is also where experience matters. Someone who has sat in real incidents knows that "tell me everything" is not useful in the first hour. You need a tight message: what happened, what's impacted, what you're doing next, and what decisions you need. If you want a sense of that kind of boardroom-ready experience, the perspective in experienced CISO leadership for high-stakes cyber moments matches the intent of an escalation model that works under stress.
Use a simple escalation ladder with triggers tied to impact, not fear
You can keep this simple without being vague. A four-level ladder works for many organizations, as long as the triggers are measurable.
This table is a practical starting point:
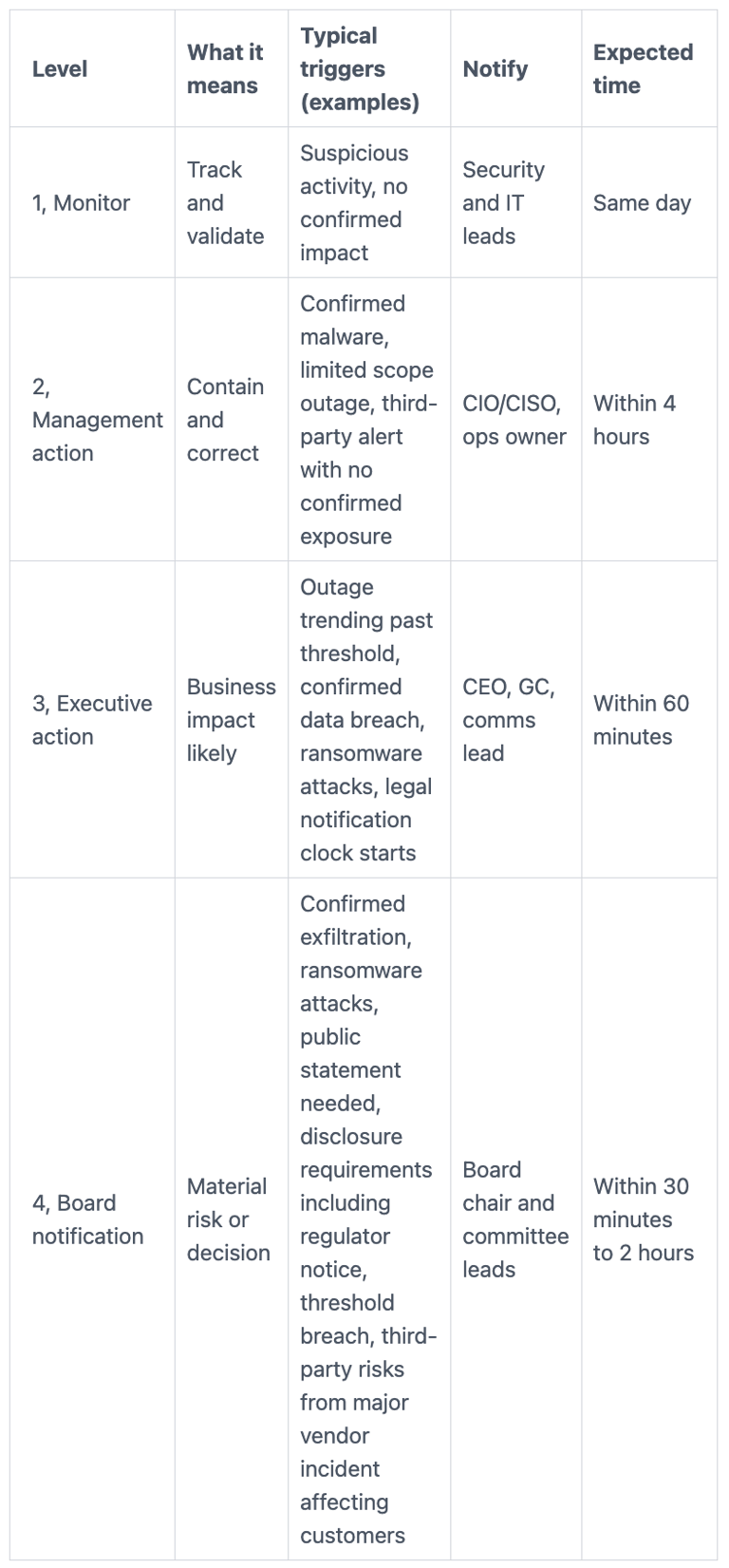
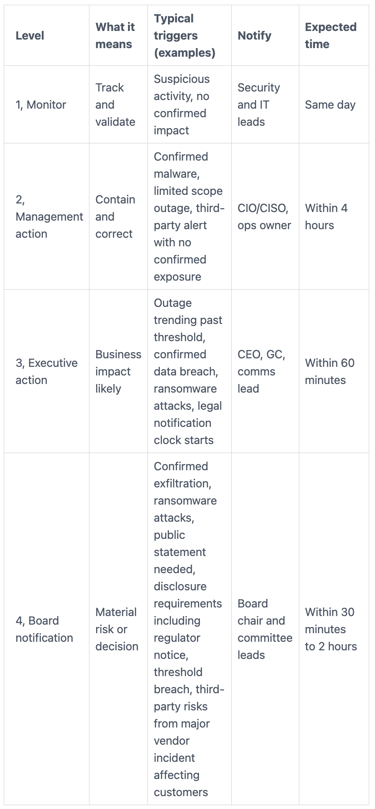
The takeaway is not the exact time values. It's that triggers tie to impact, and everyone knows what happens next.
Agree on the "first 30 minutes" rules before an incident happens
The first half hour often decides whether the next two weeks are controlled or chaotic. You can prevent a lot of pain by pre-deciding a few things.
Agree in advance on who can approve containment actions that may disrupt systems, when you engage outside counsel, when you contact your cyber insurance policy provider, who speaks externally, and who owns customer communications. Also define what the board chair needs in the first update (usually a short summary, current impact, actions underway, and next update time). Finally, set a steady update rhythm, because silence makes people assume the worst.
When your escalation rules are pre-approved, you spend incident time solving the problem, not negotiating authority.
How you know it is working, and the questions your board should ask every quarter
You'll know this work is paying off when routine decisions speed up. You'll also see fewer "surprise escalations" that arrive after a threshold was already crossed. Most importantly, you'll watch investment choices get easier, because they tie back to appetite and agreed priorities.
A quarterly governance rhythm helps the Board of Directors and Audit Committee. You review the appetite statement, check performance against thresholds, and update escalation triggers based on what changed in your business (new products, new regulators, new vendors, new threat patterns). You can keep this discussion focused without sliding into technical weeds.
If you want ongoing board-level perspectives that stay business-first, executive-focused CISO insights can help you keep the conversation grounded in decisions and outcomes, not tool chatter.
A lightweight scorecard that links risk appetite to real operations
A scorecard works when it ties cyber risk appetite to your broader Enterprise Risk Management and operational risk, and tells you where you're drifting. Keep it small enough to read in minutes. Here's a simple format you can adopt for the Audit Committee, using red,
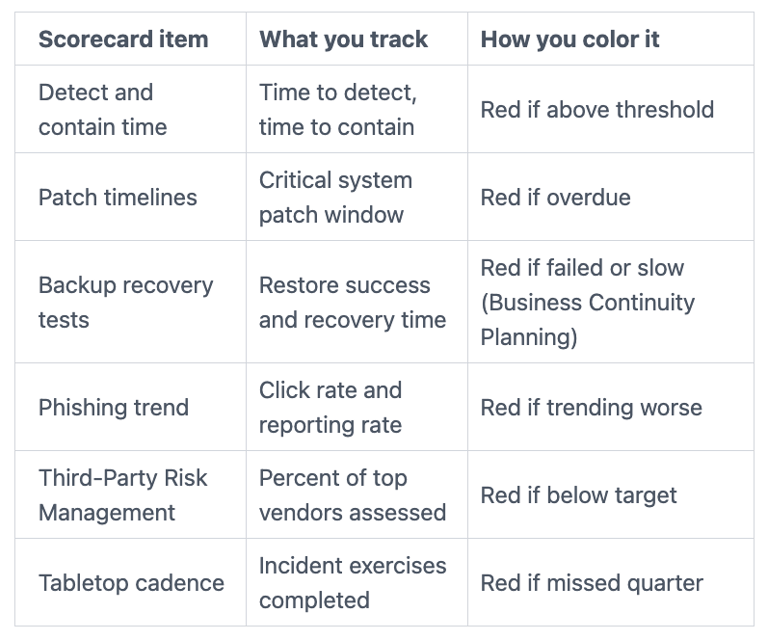
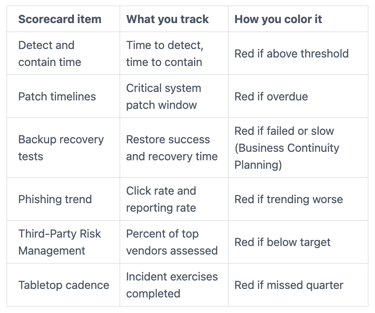
When your colors match board-approved thresholds, your cyber risk management scorecard highlights your security posture within broader risk management. The meeting shifts. You stop arguing about how to interpret risk, and you start deciding what to do about it.
Board questions that force clarity without dragging you into the weeds
Instead of asking for more charts, ask questions that test decision readiness. This governance process keeps oversight strong while letting management run the program.
Use questions like these, and require plain answers:
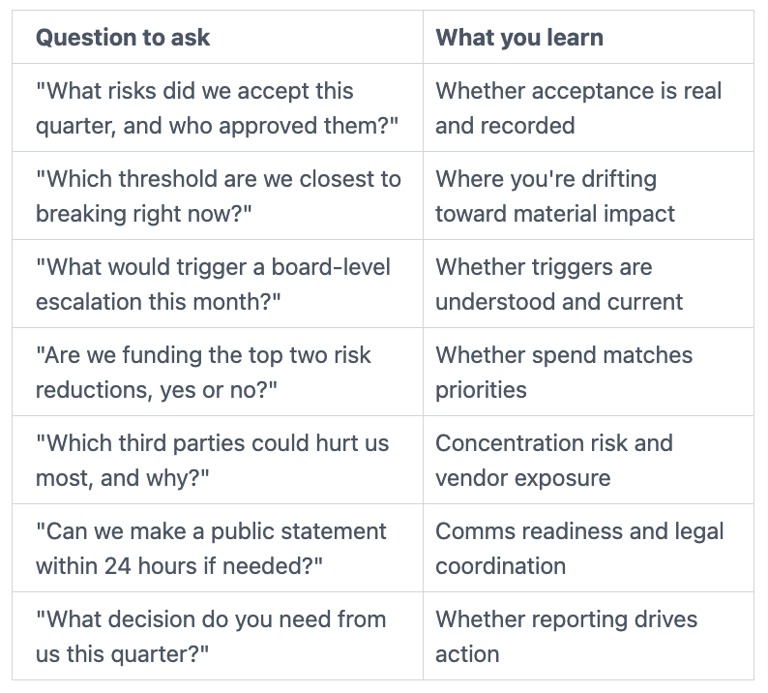
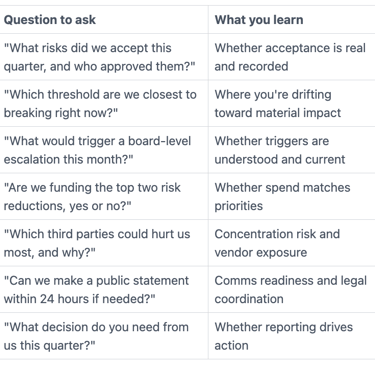
FAQs about a Board Cybersecurity Advisor, risk appetite, and escalation
Boards often hesitate to build board awareness because they don't want another layer of process. These answers keep it practical. If credentials and standards matter in your environment, you can also look at board-ready cybersecurity leadership certifications as one signal of discipline and breadth.
How is a Board Cyber Risk Advisor different from a Chief Information Security Officer or a vCISO
A Board Cyber Risk Advisor focuses on cyber risk oversight, governance, Tone at the Top, decision clarity, and board communication. A Chief Information Security Officer (CISO), the abbreviation for security leadership, or vCISO focuses on running the security program and delivering controls, people, and operations. You might need both. The cybersecurity advisor helps you set the rules and thresholds, then the CISO executes and reports against them.
How long does it take to define risk appetite and an escalation model
You can draft both in 2 to 6 weeks, depending on complexity. Often, you can get a workable first version in one workshop. Then you validate thresholds, document ownership, brief executives, train the incident team, and run at least one tabletop exercise to test escalation.
What inputs do you need to do this well
You need your business strategy, a basic crown jewels map, incident history of cyber threats, regulatory obligations, cyber insurance terms, key vendors, a Cyber Maturity Assessment, a snapshot of current controls, and a clear list of process owners. If you don't have all of that, you can still start, but you should fill gaps quickly.
Do you need a formal framework like NIST or ISO to set appetite and escalation
No. Frameworks help organize risk management work, but your board view should stay simple. Your board approves impact thresholds and escalation triggers for corporate governance. Then management maps those decisions to controls and standards to prove execution and improve maturity over time.
Conclusion: get to clarity, then test it under pressure
If you want fewer cyber surprises and stronger Cyber Risk Oversight, don't start with another dashboard. Start with two pages and one workshop: draft the risk appetite statement, draft the escalation ladder, then test both in a tabletop. This simple approach meets SEC cybersecurity rules' disclosure requirements while clarifying your strategy. After that, review quarterly to uphold your Fiduciary Responsibility and adjust as your business changes. Consider an Independent Cyber Risk Review to maintain ongoing clarity and cyber resilience.
You'll make faster calls because ownership is clear. You'll reduce stress because escalation is predictable. You'll also build stronger trust because your decisions match your promises. For a perspective grounded in continuous learning and board-relevant leadership for the Board of Directors, see an evolving and learning CISO approach.
