Board Cybersecurity Advisor: What You Actually Need (Not Another Slide Deck)
A Board Cybersecurity Advisor turns cyber updates into board decisions, a 90-day plan, and incident-ready oversight, so you cut surprises.


You sit through security updates, you nod at the charts, and you still walk out unsure what to do next as a member of the Board of Directors. That's not because you're not paying attention. It's because most cyber reporting is built to inform, not to help you make decisions.
A Board Cybersecurity Advisor is there to change that. Think of the role as an independent, business-first guide who provides independent cyber risk review to help your board handle cyber risk oversight like any other enterprise risk within risk management and enterprise risk management frameworks, all while fulfilling your fiduciary responsibility. You get clearer choices, fewer surprises, and a steady cadence that makes oversight real. If you're evaluating who can play that role, this profile is a useful reference: experienced CISO for hire.
Editorial image prompt (photo-realistic): Calm boardroom or executive meeting space, over-the-shoulder view of 3 to 5 leaders collaborating on printed incident plan and risk register, laptops open with unreadable screens, notebook and pen in hand, whiteboard with blurred shapes only, soft natural window light, deep navy and slate tones with subtle coastal blue or spruce accents, warm gold highlights, off-white neutrals, clean uncluttered premium composition, shallow depth of field, 25 to 35 percent negative space on one side for headlines, no logos, no readable text.
Negative prompt: text, words, letters, numbers, typography, captions, labels, signage, watermarks, logos, brands, readable screens, readable documents, interface mockups, QR codes, banners, headlines, icons with letters, distorted text
Key Risk Management takeaways you can use in your next board meeting
Insist on five answers: What's most likely to hurt Financial Impact, uptime, or trust, what's changed since last quarter, what decision do you need from us, what happens if we do nothing, and what's the fastest path to reduce exposure.
Ask for metrics that show direction: trends, targets, and ownership, not raw counts with no context.
Approve a 90-day plan that includes quick wins, top risks, and the board decisions management is avoiding.
Define "ready" for an incident as decision rights, contact paths, pre-approved firms, and tested backups, not an Incident Response Plan binder on a shelf.
Demand a one-page risk register with owners and due dates, then revisit the same top items until they move.
Set thresholds for escalation so you're notified early, not after the story has already formed.
Separate reporting from Cybersecurity Governance: reporting tells you what happened, governance records what you decided, who owns the fix, and when you'll review it again.
Require monthly artifacts and quarterly deep dives so oversight becomes a rhythm, not a scramble.
What a Board Cybersecurity Advisor actually does for you (week to week, not just quarterly)
A Board Cybersecurity Advisor earns their keep between meetings for the Board of Directors. They don't just review a deck. They make sure your oversight produces action, and they help management stay honest about tradeoffs as part of Enterprise Risk Management.
Week to week, you should expect three kinds of output.
First, you get decision-ready memos. Instead of "here are 47 risks," you see the few that matter, tied to money, downtime, trust, and legal exposure from a Data Breach. Second, the advisor coaches executives on how to brief you plainly, without hiding behind Technical Jargon. Third, they run follow-through. That means tracking commitments, surfacing stalled work, and escalating when risk crosses a threshold you've already agreed on.
This is where the idea of trust matters. Cybersecurity is not only about controls. It's also about whether customers, regulators, partners, and employees believe you can protect what you handle, maintain a strong Information Security Posture, and recover quickly when things go wrong. That framing is central to a digital trust expert approach, because it keeps the board focused on outcomes, not tool shopping.
If you can't tell what decision is being asked of you, you're not in governance mode yet. You're just listening.
Turn cyber risk into business decisions you can approve, defer, or decline
Boards don't "manage security." You approve risk, you fund priorities, and you hold leaders accountable. A good advisor makes those choices easier by translating technical exposure into board-level options.
In practice, you'll see decisions like these come to the surface: risk appetite and tolerance, budget tradeoffs, third-party posture, policy exceptions, cloud concentration risk, and disclosure readiness. You'll also see when a problem is really a business decision in disguise, like accepting slower product delivery to fix identity gaps.
Instead of a single recommendation, the advisor should bring two to three options. Each option should include cost, time, operational impact, and residual risk (what still stays true after you do the work). That way, you can vote without getting trapped in debates about tools, patch CVEs, or technical architecture.
When management says, "We just need more headcount," you should get a sharper question right away: "More headcount to do what, and what risk changes if we don't?"
Build a simple governance rhythm that keeps you out of surprise mode
Surprises happen when oversight is irregular. A steady cadence reduces heat and increases honesty. Your advisor should help you set a rhythm that fits your size and risk, potentially coordinating with the Audit Committee.
Use a monthly dashboard for a small set of leading indicators and open decisions. Then run quarterly deep dives on one topic at a time, such as readiness for Ransomware Attacks, cloud access, or third-party exposure. Finally, hold an annual tabletop exercise that includes the CEO, legal, comms, IT, the Chief Information Security Officer, and a board representative.
Here's a simple way to split artifacts so you don't drown in detail.
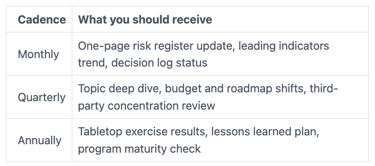
Between meetings, the advisor should track decisions, confirm owners, and push for closure. They should also agree on escalation triggers, so the CEO and board chair get the call early.
The 7 deliverables you should demand (and the red flags when you do not get them)
You're not paying for slides from an Independent Cyber Risk Review. You're paying for artifacts that move risk down and readiness up, with clear ownership. Strong advisors also bring credibility and standards-based discipline, because the work has to stand up under pressure and scrutiny. If you want a sense of that grounding, see certified to lead.
Two deliverables should exist before the "big five" below: a board decision log (what you approved, deferred, or declined, with dates) and a plain-language statement of your Risk Tolerance (what losses and downtime you will not tolerate, and what you will).
When those are missing, oversight becomes fuzzy. You end up re-litigating the same topics every quarter.
A one-page risk register you can read, with owners and due dates
Keep it short, top 10 to 15 enterprise risks. Each item should include likelihood and impact in plain terms, the main controls in place, the key gap, a target date, and an accountable executive.
A strong version ties to budgeting and audit. A weak version reads like a scan report, with no owner and no deadline.
A realistic Incident Response Plan that your board can actually use
Your plan should state decision rights, who calls who, and how outside counsel and incident response firms engage. It should also cover communications, ransomware stance, and when the board is notified per SEC Disclosure Rules.
"Ready" means contact lists are current, vendors are pre-approved, backups are tested for restore as part of Business Continuity Planning, and tabletop outcomes feed a lessons-learned loop. A weak plan is long, vague, and untested.
A small set of metrics that show direction, not noise
Ask for 8 to 12 metrics max. Separate leading indicators (Vulnerability Management metrics like patch latency, phishing resilience, privileged access coverage, backup recoverability tests) from lagging indicators (incidents, losses, downtime).
Vanity metrics are common. If you see only counts with no targets or trends, you're not seeing management.
Third-Party Risk Management and cloud concentration risk, explained without fear tactics
You should see critical vendors, a simple data-sharing map, key contract clauses for Regulatory Compliance, and exit plans. Cloud identity and access dependencies need to be clear, because one weak admin path can become a wide-open door. Consider alignment with your Cyber Insurance Policy requirements.
Good board questions are calm but sharp: "Which vendor outage would stop revenue in 24 hours?" "What's our workaround?" "Who validates controls, and how often?"
A clear 90-day plan that makes progress visible
The first 90 days should build a fact base, confirm top risks via Cyber Maturity Assessment, deliver quick wins, and surface a decision backlog for the board. It should also map to standards such as NIST or ISO in a practical way to shape your Cybersecurity Strategy, so you improve real controls, not paperwork.
If you want a model of continuous improvement that stays grounded in real operations, this perspective helps: evolving and learning CISO.
How to choose the right advisor, and how to set them up to succeed
Picking the wrong advisor feels fine until the first hard moment. Then you realize you bought comfort, not clarity or the right Tone at the Top. So, screen for independence, Board of Directors communication skill, and crisis experience. Also check for conflicts. If they sell tools, they may push tools.
Your operating model matters as much as the person when upholding fiduciary responsibility. Decide where they sit (Audit Committee, risk committee, or full board), who they brief, and how they coordinate with the Chief Information Security Officer, CIO, legal, and internal audit. If you want ongoing board-friendly viewpoints from a Chief Information Security Officer to calibrate your expectations, start here: CISO insights.
Interview questions that expose real board-level skill
How do you define "good" cyber governance? Good answer: you connect decisions, ownership, and follow-through to business risk.
Show how you brief a board in five minutes. Good answer: you lead with the decision, then the risk, then the options, avoiding technical jargon.
How do you handle risk acceptance? Good answer: you document it, quantify it, and set review dates.
What does incident readiness mean to you? Good answer: decision rights, tested playbooks, and proven recovery, not binders.
How do you measure improvement without vanity metrics? Good answer: you use trends tied to risk reduction and recovery time.
Tell us about a breach where you advised executives. Good answer: you explain choices, timing, and communication, not hero stories.
How do you deal with a defensive leadership team? Good answer: you reduce heat with facts, then set clear accountability.
How do you evaluate third-party and cloud concentration risk? Good answer: you map dependencies and define exit and failover plans.
What would you do in your first 30 days here? Good answer: you build the fact base, conduct a cyber maturity assessment, and surface decisions fast.
How do you align cybersecurity strategy with growth? Good answer: you protect critical paths (revenue, customer data, uptime) first.
Make the relationship work: access, expectations, and a decision log
Set the rules early. Your advisor needs direct access to the CEO and the committee chair. Pre-reads should be short and sent on time. Meetings should end with decisions, owners, and dates, recorded in a simple decision log.
Also clarify boundaries. The advisor doesn't replace management. They raise the bar on governance and strategic oversight, make blind spots visible, and keep the board from drifting into comfort stories.
If you want to set up a practical advisory relationship with clear expectations, start with engage CISO advisor.
FAQs boards ask about cybersecurity advisors
How is a Board Cybersecurity Advisor different from a vCISO?
A vCISO usually helps run the security program. A board advisor focuses on governance, oversight, and board decision support.
Do you need an advisor if you already have a Chief Information Security Officer?
Often yes, because your Chief Information Security Officer is responsible for delivery. An advisor adds independent challenge and board-ready framing.
What does it typically cost?
Costs vary by scope and cadence. Many boards use a fractional model, often priced monthly or per meeting cycle, rather than full-time.
How do you keep the advisor independent?
Avoid advisors who also sell security tools into your company. Require conflict disclosure and keep the role focused on governance artifacts.
Does having an advisor reduce board liability?
An advisor doesn't remove accountability. However, strong governance records (decisions, oversight cadence, and follow-through) help show you acted responsibly, especially when addressing SEC Disclosure Rules via thorough Materiality Analysis and supporting Cyber Insurance Policy claims.
How fast can you improve incident readiness?
You can improve meaningfully in 30 to 90 days if you secure decision rights, pre-approved partners, and tested recovery steps for threats like Ransomware Attacks.
What does success look like after six months?
Fewer open high-risk items through stronger Vulnerability Management, faster patch and access improvements, tested recovery that builds Cyber Resilience, ongoing Cybersecurity Awareness Training, and a board that can explain top cyber risks in plain language.
Conclusion
You don't need another slide deck. You need a Board Cybersecurity Advisor who turns cyber risk into decisions, sets a steady Cyber Risk Oversight rhythm, and drives measurable follow-through. By establishing the right Tone at the Top, the Board of Directors ensures surprises drop and accountability rises. In the next 30 days, pick two deliverables from the list (start with the one-page risk register and the incident plan) and ask to see them, with owners and dates. Then keep those same items on the agenda until they change.
