Do CEOs Need a Cybersecurity Strategy Advisor? 8 Signs You’re Carrying Silent Risk
See 8 signs you're carrying silent risk and what to fix first. A cybersecurity strategy advisor for CEOs brings focus, owners, and board-ready metrics.


You probably don't lack security tools. You likely lack clear ownership, tight priorities, and decision support that fits how a CEO actually runs a business. That's where silent risk grows, not in the obvious places like antivirus or firewalls.
A cybersecurity strategy advisor connects your business goals to security choices, risk limits, and readiness. They help you decide what matters first, who owns it, and what "good enough" looks like this quarter. Silent risk tends to build during growth, M&A, vendor sprawl, AI adoption, or rapid product shipping, because change outruns governance.
This post gives you eight practical signs you can check this week. For each sign, you'll see what it means in business terms and what to do next. You won't get fear tactics. You'll get a clearer way to run security like the rest of the business: with focus, accountability, and measurable progress.
Key takeaways for busy CEOs
You need decision support that ties cyber risk to revenue, downtime, legal exposure, and trust.
Hidden risk often shows up in meetings, not in dashboards.
The first win is clarity, your top risks, your crown jewels, and who owns each risk.
In 30 to 60 days, you should have a short roadmap you can fund and track.
You should be able to explain risk in dollars and hours, not tool names.
Board updates should drive action, not confusion or false comfort.
Practiced incident response matters more than a perfect policy binder.
What a cybersecurity strategy advisor does, and what they are not
Think of this role like a "flight director" for cyber risk. You still have pilots (IT, engineering, security ops). You still have air traffic control (compliance, legal, audit). The advisor makes sure everyone is working the same plan before you hit turbulence.
A cybersecurity strategy advisor for CEOs helps you set direction and reduce surprise. In practical terms, they:
Create a simple view of your top risks and what drives them.
Turn scattered security work into a ranked roadmap tied to business goals.
Align leaders who rarely agree on security (product, IT, legal, finance).
Improve oversight, so you can govern security without living in it.
Prepare board-level reporting that is clear, honest, and usable.
They are not IT support, and they are not there to "run tickets." They're also not a compliance-only consultant who treats an audit as the finish line. A good advisor won't sell you a tool as the answer, either. Tools can help, but they don't set priorities, settle tradeoffs, or assign ownership.
You can bring this support in different ways: fractional (a few hours a week), interim (during a gap), or board-facing (to help with oversight and reporting). If you need a leader who can translate risk into executive action, you can also explore an experienced CISO for hire who can operate at CEO and board level.
The outcomes you should expect in plain language
You're paying for fewer surprises and faster decisions. Outcomes should look like:
Clear top risks: You know what can hurt you most, and why that matters to the business.
A prioritized plan: Spending and staffing choices follow a ranked roadmap, not the loudest request.
Incident readiness: People know roles, legal steps, and how to keep operations moving.
Vendor risk handled: Your biggest third parties are tiered, reviewed, and contract terms improve.
Board-ready reporting: Updates focus on exposure, progress, and decisions needed.
Fewer "mystery outages": Identity, access, and change control get cleaner, so production breaks less.
If you can't explain what you're protecting, who owns it, and what you'll do when it breaks, you don't have a strategy yet. You have activity.
When it is smarter to use an advisor instead of waiting to hire a full-time CISO
Waiting can cost more than hiring. An advisor often makes sense when you're moving fast but lack stable leadership. That includes rapid growth, your first real compliance deadline, a recent incident or near miss, a CISO gap, or an M&A integration. It also fits when customer trust is part of the product, such as B2B SaaS, fintech, health, education, or marketplaces.
8 signs you are carrying silent cyber risk
Silent risk is like unmarked debt. It doesn't show up until interest spikes, a lender asks questions, or you try to sell the company. These signs help you spot it early, while you still have choices.
The first four signs show up in decisions, not dashboards
1) You cannot name your top 5 cyber risks in one minute (and neither can your leaders)
If you ask five leaders, you get ten answers. That's a signal you don't have shared risk language.
What it sounds like in a meeting: "We have a lot of risks, but I'm not sure which ones are the big ones."
Why it matters: You can't fund, delegate, or accept risk you can't name.
Practical fix: Build a one-page risk brief with your top five risks, each with an owner, impact (in dollars or downtime), and a next step. Review it monthly.
2) Security work is a pile of projects, not a ranked roadmap tied to business goals
You see activity everywhere, but you can't tell what it adds up to. Teams ship controls because someone asked, not because it reduces a top risk.
What it sounds like in a meeting: "We're doing 14 security projects, but I don't know which ones are must-do."
Why it matters: You spend money without reducing the risks that can stop growth.
Practical fix: Tie every security initiative to one business goal (ship faster, reduce outages, win enterprise deals) and one risk it reduces. Then rank the work.
3) You rely on "we are compliant" as proof you are safe
Compliance can be helpful, but it's a minimum bar. It rarely proves you can handle real attacks or real failures.
What it sounds like in a meeting: "We passed the audit, so we're good."
Why it matters: You may still be exposed to account takeover, ransomware, or data loss, even with a clean report.
Practical fix: Add a simple risk register next to compliance. Use it to track real exposures, not just audit items. Keep it short and used.
4) Your board updates are either too technical or too vague to act on
Some updates drown directors in acronyms. Others say "we're fine" without evidence. Either way, the board can't steer.
What it sounds like in a meeting: "We improved our SIEM rules and EDR coverage," followed by silence.
Why it matters: Oversight breaks down, and you lose the chance to get support before a crisis.
Practical fix: Define three to five board metrics that map to outcomes, such as time to revoke access, backup recovery time, phishing-resistant MFA coverage, and vendor tiering progress. If you want a model for business-first cyber communication, the business side of cybersecurity is a useful reference point.
The next four signs show up when something changes or goes wrong
5) You do not know your "crown jewels" (most critical systems and data) and who can access them
If your team can't answer "what must never go down" and "what must never leak," you're guessing. Crown jewels change as products and vendors change.
What it puts at risk: Revenue and operations, because the wrong outage can stop fulfillment, billing, or production.
First step in 2 weeks: List your top 10 systems and datasets, then mark which ones would stop revenue within 24 hours. Identify who has admin access.
What "good" looks like in 90 days: Crown jewels are documented, access is reviewed, logging is enabled, and backup recovery is tested for those systems first. If you want a trust-first way to frame this for customers and boards, think in terms of outcomes described by a digital trust expert for CEOs.
6) Vendors and SaaS apps grew fast, but third-party risk reviews did not
Your company can become a network of SaaS logins. Meanwhile, procurement moves faster than security reviews. That gap becomes your exposure.
What it puts at risk: Trust and legal exposure, because vendor incidents can become your incident.
First step in 2 weeks: Build a vendor inventory from finance and SSO logs. Tier vendors by data sensitivity and business impact.
What "good" looks like in 90 days: Tier-1 vendors have basic controls verified (SOC 2 or equivalent), contract security terms are standard, and offboarding steps exist. You also know which vendors can reach production systems.
7) Incident response is a document, not a practiced routine (no tabletop in the last 12 months)
A plan you've never practiced is a story, not a capability. Under stress, people don't rise to the plan, they fall to their habits.
What it puts at risk: Downtime and costs, because confusion adds hours, and hours add dollars.
First step in 2 weeks: Schedule a 60-minute tabletop with your CEO delegate, IT, product, legal, and comms. Pick one scenario: ransomware, data leak, or major SaaS outage.
What "good" looks like in 90 days: Roles and decision rights are clear, outside counsel and forensics are pre-selected, and you can run a tabletop in under two hours with clean follow-ups.
8) Identity and access feels messy (shared accounts, weak offboarding, too many admins, unclear MFA coverage)
Identity is the front door to almost everything now. If access controls are messy, every other control works harder.
What it puts at risk: Revenue and trust, because account takeover can lead to fraud, outages, or data exposure.
First step in 2 weeks: Pull a list of admins, shared accounts, and MFA coverage. Fix the worst offenders first (ex-employees, shared admin accounts, no MFA on email).
What "good" looks like in 90 days: Offboarding is reliable, admin roles are limited, privileged access is tracked, and phishing-resistant MFA covers your most sensitive systems.
A simple rule helps: if you wouldn't hand someone the company credit card without a process, don't hand them admin access without one.
How to decide if you need an advisor, and how to pick the right one
A clean decision path is this: when risk is high, clarity is low, and change speed is high, you need help. Many CEOs feel this when sales is pushing into enterprise, product teams are shipping weekly, and vendors keep piling up.
To pick the right person, don't start with tools. Start with decision outcomes. You should be able to forward these requirements to your COO or GC:
A top-risk view tied to business impact (dollars, downtime, trust).
A 90-day roadmap with owners, costs, and dependencies.
A board-ready reporting format and a monthly governance rhythm.
An incident readiness check plus a tabletop exercise.
A vendor tiering method and contract minimums.
Identity and access quick wins that reduce real exposure.
If you want to talk through fit and expectations without committing to a full-time hire, you can engage fractional CISO advisor support to build clarity fast.
A simple decision test you can run in 15 minutes
Score each area as Low, Medium, or High risk based on today, not your plans.
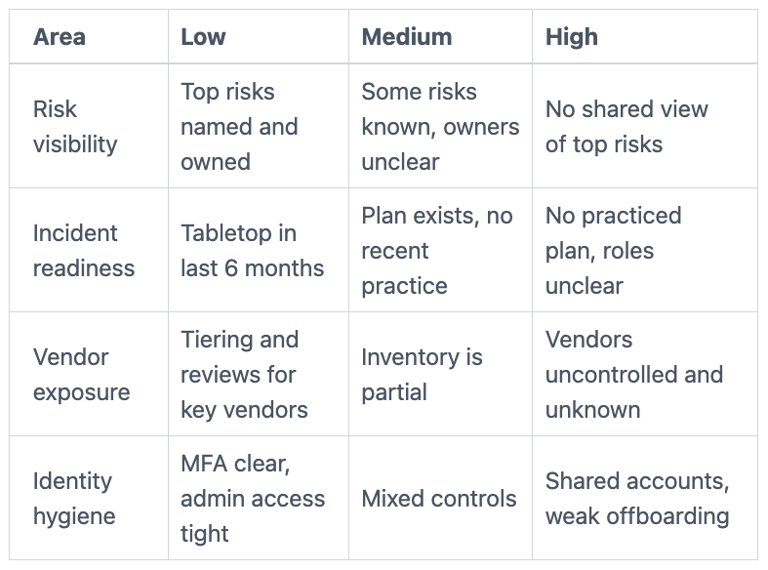
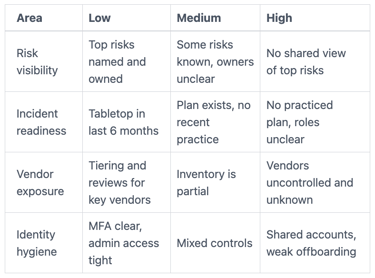
If you score one High, treat it as a priority. If you score two or more High, bring in strategy help now, because the "unknown unknowns" will cost more later.
Interview questions that reveal real strategy skills (not just tools knowledge)
How do you tie security priorities to revenue goals and product timelines?
What does your first 30 days look like, and what artifacts will you deliver?
How do you explain cyber risk to a board in dollars and downtime?
Which framework do you prefer (NIST, ISO), and how do you keep it simple?
How do you rank security work when everyone says their project is urgent?
What identity and access fixes do you tackle first in a messy environment?
How do you handle third-party risk without blocking procurement?
What does a good tabletop exercise look like, and who must attend?
How do you measure progress without vanity metrics?
Tell me about a time you reduced risk while the company was shipping fast.
FAQs CEOs ask before bringing in cybersecurity strategy help
How is a cybersecurity strategy advisor different from a CISO, MSP, or compliance consultant?
An advisor focuses on direction and decisions, especially when you need clarity and alignment. A CISO owns the security function and drives execution across teams. An MSP runs operations, such as monitoring, patching, and support. A compliance consultant prepares you for audits and evidence.
Sometimes one person can cover multiple lanes, especially in smaller companies. Still, you should be clear about the job to be done. If you need executive ownership and board communication, you're closer to CISO work. If you need a short, focused plan and better oversight, an advisor can fit well.
How fast will you see value, and what should the first 30 days include?
You should see value quickly, because the first win is focus.
In the first 2 weeks, expect discovery and a simple risk view. In 30 days, expect a prioritized roadmap and an incident readiness check. By 60 to 90 days, you should have a governance rhythm, improved identity controls, and a vendor tiering approach.
Common artifacts include a one-page risk summary, incident roles and contact paths, a shortlist of crown jewels, vendor tiers, and identity quick wins. If credentials and standards matter for your stakeholders, it also helps to work with someone certified to build enterprise security strategies.
Conclusion
You don't need perfection. You need visibility, ownership, and a plan your leaders can actually run. Silent risk grows when change outpaces clarity, and most CEOs feel that pressure during growth, M&A, and vendor expansion.
If several signs in this post match your week-to-week reality, a cybersecurity strategy advisor for CEOs can help you set priorities, reduce surprise, and protect trust without slowing the business.
Pick two signs to validate this week. Run one tabletop in the next 30 days. Then assign owners to your top risks, with dates and outcomes, not just tasks.
