What an Experienced CISO Fixes First in a Fragile Security Program
See what an Experienced CISO fixes first in a fragile security program: ownership, identity, hardening, logging, and a scorecard leaders trust.


You can feel when security exists, but it's thin, especially during rapid Digital Transformation. Things "work" until they don't. A vendor questionnaire shows gaps you can't explain. An alert fires at 2 a.m., and you're not sure who's on point. Your team is busy, yet you don't feel safer.
A fragile Information Security Program usually looks like this: too much hero work, unclear ownership, unknown exposure, and controls that change by team or tool. It's easy to break because it depends on memory, not repeatable habits.
An experienced Chief Information Security Officer doesn't start by shopping for more tools. The first moves are about clarity and control to build a solid Security Strategy, so you can reduce risk fast without boiling the ocean. If you need proven Cybersecurity Leadership quickly, consider a Virtual CISO to stabilize priorities and execution while you decide what comes next.
Key takeaways: the first moves that stabilize a fragile information security program
Decide what matters most, then protect it first (not everything equally).
Confirm governance for who owns each major risk in risk management, and who can accept tradeoffs.
Shrink the easiest breach paths, starting with identity and privileged access.
Standardize basic hardening to improve your security posture, so security isn't different in every corner.
Get logging and response working end to end, with real escalation.
Practice incident response decisions, so your plan isn't just a document.
Track progress with a small scorecard tied to business outcomes.
If you want more practical guidance you can apply right away, browse CISO insights.
Step one is clarity: what you protect, what you can lose, and who decides
A fragile program fails in a predictable way: work piles up, but choices stay fuzzy. You patch what's loud, not what's risky. You fund what's urgent, not what matters. Meanwhile, nobody can answer simple questions like, "If this system goes down, what breaks first?"
An Experienced CISO starts with effective Risk Management by making risk visible in plain language, laying the foundation for a clear Security Strategy, then forcing the few decisions that unblock everything else.
First, you identify your "crown jewels." That might be customer PII, payment flows, a manufacturing line, a donor database, or the system that runs payroll. If you can't name them, you can't defend them.
Next, you map the business processes that create value and drive your Business Objectives. Think of it like tracing the water lines in a building. You don't protect every pipe the same way. You protect the ones that flood the whole place.
Then you conduct a focused Risk Assessment to outline the most likely attack paths. Not a long threat model, just the common routes that keep showing up:
account takeover through weak authentication,
privileged access sprawl,
exposed remote access,
unpatched internet-facing systems,
vendor access that never goes away.
Finally, you set risk appetite with Executive Leadership, including C-suite Executives. That sounds formal, but it can be simple: what downtime is tolerable, what data exposure is unacceptable, and what spending you'll support to avoid repeat pain.
When you can't say who decides, you don't have a security program, you have a debate club.
This clarity establishes proper Governance. It stops random work and gives the Board of Directors clear risk reporting. It also gives you a way to align spend, because you can connect each action to a business loss you're avoiding.
Fix the biggest "easy to break" weaknesses: identity, access, and basic hardening
If your program feels fragile, attackers probably see it the same way. They don't need to beat your best controls. They only need one weak doorway, and identity is usually that doorway, especially amid the rapid digital transformation that has shifted modern identity challenges.
An Experienced CISO typically prioritizes identity and access first (after a risk assessment shows their outsized impact) because it reduces breach success quickly. It also reduces blast radius when something goes wrong.
In weeks 1 to 4, you focus on the highest-impact basics:
You tighten privileged access. That means fewer admins, clearer approval, and short-lived elevation where possible. Shared accounts get eliminated or controlled. Break-glass access gets monitored and tested, not guessed.
You expand MFA where it matters most. Email, remote access, admin consoles, and any path to production systems come first. Coverage percentage matters less than protecting the accounts that can cause the most damage.
You clean up account sprawl. Stale accounts, contractors, and "temporary" access are common. Removing them is boring work that pays off. It's also a leadership signal that rules apply consistently.
You standardize baseline hardening using frameworks like the NIST CSF. Fragile programs often have ten different "standards" depending on who built the server. You need one minimum bar, backed by security policies that support compliance, for:
patching expectations for critical systems,
secure configuration for endpoints,
basic segmentation for sensitive systems,
secure remote access patterns.
Later (after week 4), you tune for depth. Vulnerability management becomes more targeted. You add stronger controls around secrets, CI/CD pipelines, and cloud posture. Those matter, but they're not the first domino.
The goal early is simple: make common breach paths fail more often.
Get detection and response working like a muscle, not a binder on a shelf
Many fragile programs already own tools. They have an EDR agent, a SIEM, maybe even a SOC contract. Yet the signal is weak, and response is uncertain. Alerts go to an inbox. Tickets sit. Escalation depends on who happens to be awake.
An Experienced CISO treats detection and response like a muscle to make data breach paths fail. You build it through repetition, not documentation.
Start with "good enough" visibility. You don't need perfect logs from every system in month one. You need reliable coverage for the systems that matter. That typically means:
identity events (logins, MFA changes, privilege changes),
endpoint security events,
critical cloud control plane logs,
key server and application logs to ensure strong security posture for crown jewels.
Then you define what "severe" means. Without that, everything feels urgent, and nothing gets handled well. A simple severity model, agreed with IT and leadership in line with ISO 27001, prevents constant re-triage.
Next, you set a clear escalation path. Who gets called for suspected ransomware? Who can approve isolating a system? Who briefs legal and comms? The answers must be written down, and they must work after hours.
A short tabletop exercise builds your incident response muscle fast. You simulate an incident and watch where the handoffs fail. Most gaps are not technical. They're human, such as unclear decision rights, missing contacts, and slow evidence collection.
Your incident plan doesn't protect you, your practiced decisions do.
When this improves, executives feel it. They stop hearing vague updates like "we're investigating." Instead, they get calm statements about scope, impact, and next actions. This fosters business resilience.
Prove progress in business terms with a simple scorecard executives can trust
In a fragile program, reporting often creates more confusion. Dashboards show green boxes, but leaders still feel exposed. Or metrics are so technical that the board can't tell what changed.
An Experienced CISO earns confidence from Executive Leadership with a small scorecard that ties to outcomes of the Information Security Program. The point isn't to impress. It's to make decisions easier.
Here's the kind of scorecard that works because it connects to business risk:
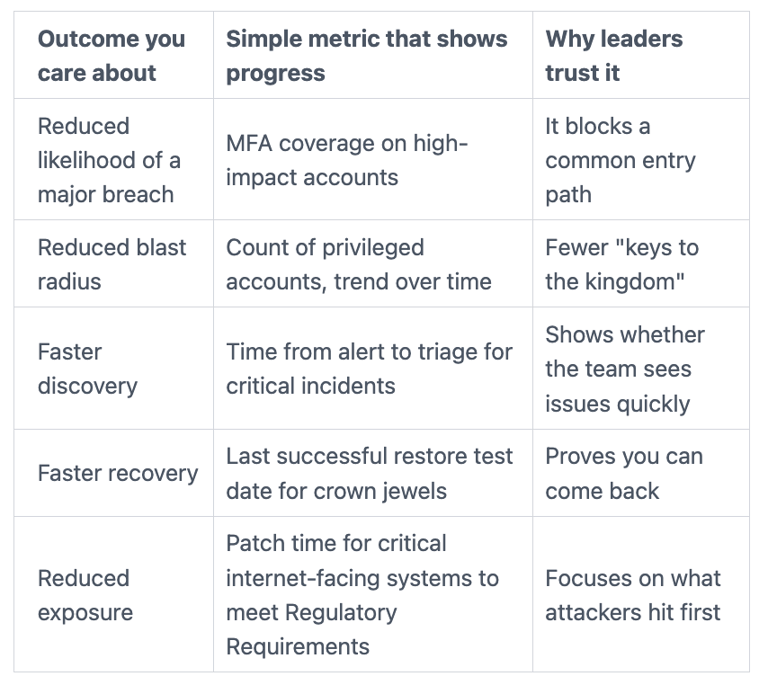
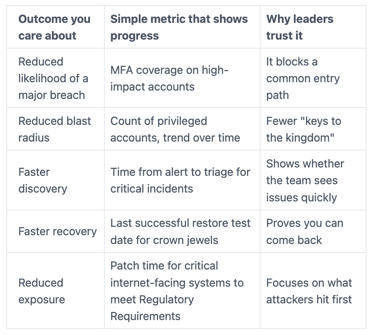
You set a cadence that matches decision-making. Weekly for operational leaders, monthly for executives, and quarterly for the Board of Directors (or the audit/risk committee). Stability matters. If metrics change every month, they stop being useful.
Also, you keep one space for uncomfortable truth. For example, "Top risks we're accepting right now." That prevents surprise, supports Compliance by satisfying auditors, and makes funding discussions more honest.
When reporting improves, budgets stop feeling like guesswork. This scorecard guides your Security Strategy, so you can explain what you're buying, and what loss it prevents.
FAQs about what an experienced CISO prioritizes in a fragile security program
How fast will you see results?
You'll often see meaningful reduction in "easy to break" risk in 30 days, especially in identity, access cleanup, and incident readiness. Larger architecture fixes take longer, but early wins should be visible quickly.
Should you buy new security tools right away?
Usually not. First, you confirm what you already own, what's deployed, and what's actually used. Then you close process and ownership gaps. Tools come later, when you can explain the outcome you need.
What if IT is overloaded and can't take on more work?
You narrow scope hard. You pick the few controls that reduce the most risk, such as Disaster Recovery and Business Continuity planning, then you stop low-value work like unchecked Security Awareness Training. A fragile program often fails because everything is "priority one." You can't fix that with more tickets.
How do you handle compliance pressure without turning security into paperwork?
You map Regulatory Requirements to a few real controls and Security Policies, then collect evidence as a byproduct of doing the work. When you focus on identity, logging, and response, you usually cover a lot of Compliance ground without creating a separate world of checklists.
When should you hire interim or fractional help?
You hire a Fractional CISO or Virtual CISO when risk is rising faster than your leadership capacity. Common triggers include an audit failure, a breach or near miss, rapid growth, a major platform change, or a CISO gap. The deciding factor is whether you can make and execute hard security decisions in the next 30 to 90 days.
What should you ask when you're hiring or evaluating a CISO?
You focus on judgment, business alignment, and crisis leadership, not just certifications. This guide on how CEOs should vet a CISO helps you separate confident talkers from proven leaders. Ask when hiring or evaluating a Chief Information Security Officer.
What if you're not sure what "good" looks like in the interview?
You use structured questions that reveal how the candidate thinks under pressure, and how they partner across the business. Start with these CISO interview questions for CEOs and CHROs.
Conclusion
A fragile security program doesn't need perfection first. It needs order. An experienced CISO with CISSP credentials stabilizes the program in a practical security strategy: clarity and ownership, identity and hardening, detection and response practice, then a simple scorecard leaders can trust.
You don't have to fix everything this quarter to reduce risk fast. You just have to stop guessing, close the easiest breach paths, and build repeatable response.
If you need an experienced Chief Information Security Officer to stabilize the program quickly, consider interim security executive support from a Strategic Advisor to drive decisions and traction while you plan the longer-term path.
