Hiring an Interim CISO in NYC. 9 Questions That Separate Real Leaders From Resume Padding
Hiring under pressure? Use 9 interview questions to spot a real Interim CISO in NYC, validate fast with references, and get a 90-day plan that works.


When you hire a Chief Information Security Officer in New York City, you're usually doing it under pressure. A sudden resignation, an audit deadline, a vendor incident, a board that wants answers, or a growth plan that can't wait. Add regulated industries, vendor-heavy tech stacks, hybrid work, and fast procurement cycles in New York's competitive business landscape, and you don't have room for a learning curve.
That's why choosing an Interim CISO in NYC is less about pedigree and more about judgment. You need a CISO who can walk in, calm the room, and move the work forward without drama. In Manhattan's high-pressure security hiring environment, an interim CISO must hit the ground running to address New York's unique talent market demands.
Below is a practical way to spot real CISO leadership fast, using nine interview questions and a simple verification method you can finish in a week.
Key takeaways you can use in the first interview
These nine questions are designed to reveal the things resumes hide:
Execution: What a CISO does in the first 10 days, not what they "plan to assess."
Judgment: How a CISO slows down risky work without becoming a blocker.
Communication: Whether a CISO can brief a NYC board on cybersecurity and Information Security in plain language.
Governance: How a CISO assigns ownership so Information Security isn't "Information Technology's problem."
Incident readiness: Whether a CISO rehearses, coordinates, and documents.
Metrics: If a CISO uses numbers to drive decisions, not dashboards.
Culture: How a CISO earns trust with engineering, legal, and Security Operations.
Vendor control: How they reduce third-party risk without freezing delivery.
Transition plan: Whether they leave a system that works without them.
If you want more executive-level framing for these conversations, use the business side of cybersecurity as a reference point for what good looks like.
Editorial image prompt (photo-realistic)
Photo-realistic editorial image prompt: Calm, focused New York office meeting with three to five professionals, including a CISO, collaborating around a conference table, over-the-shoulder angle showing hands reviewing printed plans (pages turned away, no readable text), a laptop with an unreadable screen, a notebook, and a whiteboard in the background with blurred shapes (no legible writing). Soft natural window light, gentle contrast. Color grading with deep navy and slate undertones, subtle coastal blue or spruce green accents, warm gold highlights, off-white neutrals. Clean, uncluttered, premium composition with shallow depth of field and 25 to 35% negative space for blog headlines. No logos, no brand marks, no UI screenshots, no futuristic props.
Negative prompt: text, words, letters, numbers, typography, captions, labels, signage, watermarks, logos, brands, readable screens, readable documents, interface mockups, QR codes, banners, headlines, icons with letters, distorted text
Before you ask anything, get clear on what "interim" must deliver in 90 days
"Interim" should mean outcomes, not just a shorter contract.
In NYC, the first 90 days often decide whether you stabilize risk or compound it. A strong interim CISO will ask about your business goals, regulatory exposure and compliance needs, and current friction points. Then they'll translate that into a plan your exec team can follow.
A simple 30-60-90 structure works well for risk management:
First 30 days (stabilize and listen): confirm what's on fire, verify basic controls, find the real decision-makers, and stop the riskiest behavior through initial risk management steps.
Next 30 days (assess and prioritize): create a short risk picture, align on top priorities for risk management, and set a weekly operating rhythm.
Final 30 days (start fixes and prove momentum): launch the highest-return improvements, tighten incident readiness, and set up governance that sticks.
Common trigger events include breach recovery, audit findings with compliance deadlines, M&A integration alongside your Chief Technology Officer, a cloud migration that outran guardrails with input from the Chief Technology Officer, or a leadership gap that's starting to show. If you're hiring for that kind of pressure, you'll want an experienced CISO for hire who can switch between board expectations and operational reality without losing either.
A useful test is simple: can the CISO describe what changes in 30, 60, and 90 days, using your business language?
The fastest way to tell if you need an interim CISO, fractional help, or a permanent hire
You can make this decision with three inputs: urgency, complexity, and internal capacity in information technology.
If you need a leader this month, and you have multiple stakeholders (legal, compliance, product, vendors, board committees), interim CISO coverage is often the right move. You're buying focused leadership, fast.
Fractional CISO help fits better when the program is mostly stable, but you need senior guidance for a few key items. For example, you might be preparing for a new client security review cycle, updating policies, or tightening vendor onboarding.
Permanent CISO hiring makes sense when you're building a long-term program and you can wait for the right fit. In contrast, post-incident recovery is rarely a "wait and see" moment. Neither is a regulator letter with a short deadline.
What you should expect them to produce, artifacts not promises
You don't need a glossy strategy deck first. You need working outputs that reduce confusion from the CISO.
Ask for tangible deliverables like:
A refreshed risk register (lightweight is fine) focused on risk management with clear owners
A one-page top risks brief you can use with the board
An incident tabletop plan and schedule (with who attends and why)
A vendor risk triage list (who matters most, what changes first)
A 90-day security strategy roadmap with costs, owners, and dates to support information technology governance
A policy exceptions process so teams can move without hiding
The goal is momentum you can measure, not activity you can't.
9 questions that expose real interim CISO leadership in NYC
These aren't trick questions. They're filters. Each one forces the CISO candidate to show how they think, decide, and communicate when time is tight.
Question 1: "In your first 10 business days as interim CISO, what do you look at first, and why?"
What a strong answer sounds like: You hear a short sequence: listen first, confirm current incidents with threat intelligence, identify crown jewels using threat intelligence, map compliance deadlines, then test a few basic controls (identity, backups, logging, vendor access). They mention meeting business leaders, not just IT, and flag modern technical risks like artificial intelligence deployments.
Red flags: Tool shopping on day one, "I assess everything," or no mention of people, priorities, or threat intelligence.
Follow-up probe: "Which two meetings do you schedule in week one to learn the real risk story as interim CISO?"
Question 2: "Tell me about a time you stopped a high-risk project without becoming the 'no' person, as an interim CISO."
What a strong answer sounds like: They describe trade-offs, options, and timing. They might say, "We paused the launch, added a compensating control, and set a two-week path to restart." They show respect for delivery teams while holding a firm line on risk.
Red flags: Pride in blocking, blaming engineering, or vague statements like "I escalated and shut it down."
Follow-up probe: "What did you offer as a safer alternative, and what did it cost, from your CISO perspective?"
If you want the mindset behind this style of leadership, look for someone who treats security as trust-building, not control theater, like a digital trust expert for boards.
Question 3: "How do you explain cyber risk to C-level peers on a New York board in five minutes?"
What a strong answer sounds like: Plain language, a few risk scenarios, and a clear ask. They connect risk to money, downtime, legal exposure, and customer impact. They keep it tight and propose decisions, not lectures.
Red flags: Jargon, fear tactics, or "I'd show them our dashboard."
Follow-up probe: "Give me a sample outline of a single board slide from the interim CISO, what are the three bullets and the decision?"
Question 4: "Walk me through how you run incident readiness for cyber resilience, even if nothing is on fire today."
What a strong answer sounds like: Roles, runbooks, and rehearsal. They mention legal, PR, and exec communications. They also bring up vendor contacts, escalation paths, and the basics that make cyber resilience possible (logs, backups, access control).
Red flags: Tool-only answers, no tabletop exercises, or "we'll figure it out during the incident."
Follow-up probe: "Who owns the 'business decision' during an incident, and how do they get informed by the CISO?"
Question 5: "What is your method for deciding the top 5 risks as interim CISO, and who owns each one?"
What a strong answer sounds like: A simple method: impact plus likelihood, tied to business goals. They name owners in the business, not just in security. They also set deadlines and revisit the list often, including risks from artificial intelligence.
Red flags: "Security owns all risks," no prioritization method, or a list of 20 "top five" items.
Follow-up probe: "Show me how you'd assign ownership for vendor risk as CISO, is it procurement, product, or legal?"
Question 6: "How do you handle a tough New York audit or regulator request when the house is not in order?"
What a strong answer sounds like: Honest scoping, careful evidence handling, and a clear remediation plan. They explain how they communicate gaps without panic, then track fixes with dates and owners. They might reference NIST or ISO as organizing structures, but they keep it practical.
Red flags: Hiding issues, attacking the auditor, or promising timelines they can't control.
Follow-up probe: "What do you put in writing, and what do you keep verbal during the first week, as interim CISO?"
Question 7: "Which security metrics do you use so C-level peers actually take action?"
What a strong answer sounds like: A few metrics that drive decisions and show trends. You might hear MFA coverage, patch time for critical systems, backup restore test success, phishing reporting rates, and critical vendor status. They tie each metric to an owner and a meeting cadence.
Red flags: Vanity metrics, dozens of charts, or "we track everything."
Follow-up probe: "Which metric do you review weekly with the COO as CISO, and what decision does it trigger?"
Question 8: "How do you take control of vendors and consultants without slowing the business in New York?"
What a strong answer sounds like: Inventory, tiering, and contracts. They partner with procurement and legal. Reviews match risk, so low-risk tools don't face high-friction gates. They also mention offboarding access and tightening third-party admin paths.
Red flags: Rubber-stamping vendors, blocking everything, or no awareness of contract terms.
Follow-up probe: "What clauses or requirements do you push for first when time is short, as interim CISO?"
Question 9: "If you do great work here as CISO, how will you hand it off so we do not backslide?"
What a strong answer sounds like: Documentation, operating rhythm, and clear ownership. They describe how they'll build a repeatable cadence, teach the team, and leave a roadmap that survives leadership changes for ongoing cyber defense. They also set expectations for what you must keep doing after they leave to sustain cyber defense.
Red flags: Creating dependency, no written decisions, or "my team will handle it" when there is no team.
Follow-up probe: "What are the three artifacts you'll leave behind that prove you were here and bolstered cyber defense?"
If you want to formalize that handoff and keep momentum, consider engaging an advisor to support the transition and maintain executive oversight.
How you verify the answers fast, references, work samples, and a simple scorecard
You can validate an interim CISO candidate without dragging out the process. Plan for a one-week sprint: one deep interview, one peer panel with a Vice President, Director, and Senior Director, two reference calls, and two work samples.
Use a simple scorecard so you don't get swayed by charisma. Here's a format that works well in practice for evaluating CISO candidates:
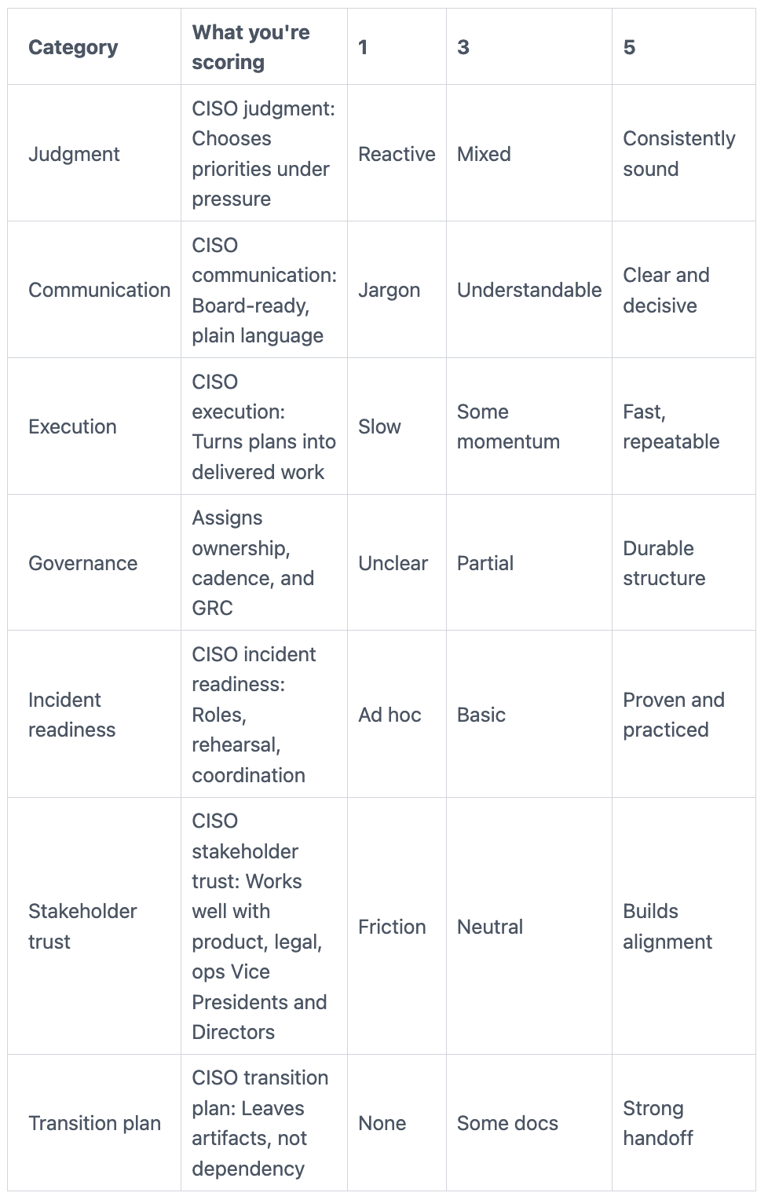
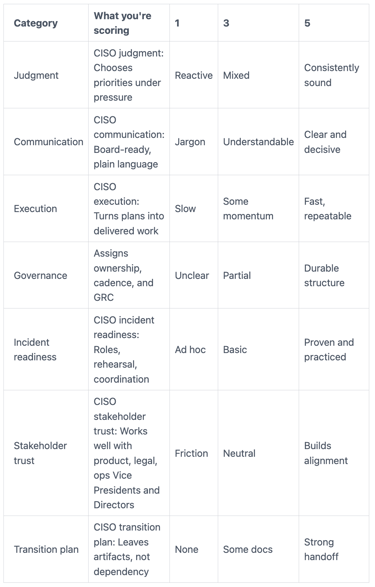
The goal isn't perfection. You're looking for a pattern of clarity, follow-through, and calm CISO leadership.
Reference questions that get past polite praise
Most references default to "They were great." You need prompts that force specifics on CISO performance, especially for high-scrutiny roles where Global CISO-level references matter:
"What changed in the first 60 days because of their CISO work?"
"What did they simplify that had been stuck for months as CISO?"
"Where did they struggle, and how did they respond?"
"How did they handle conflict with product or engineering Senior Directors?"
"Did they improve trust with executives, or just add process?"
"What did they leave behind that still runs today?"
"Would you bring them into a high-scrutiny board situation again?"
Listen for concrete outcomes and steady behavior, especially under stress.
Work samples you can request without exposing sensitive data
Through your professional network, you can ask for samples that prove CISO method without exposing your systems. Keep it respectful, and use an NDA if needed. Peers in your professional network can also help verify these.
Acceptable requests include an anonymized 30-60-90 plan, a sample board risk memo, a tabletop exercise agenda, or a sample risk triage approach. What matters is how they structure decisions, not your confidential details.
Conclusion: hire for outcomes, then lock in the cadence
A strong interim CISO doesn't win with buzzwords. They win by setting priorities, building trust, and producing artifacts your team can run, including assessments of your technical infrastructure. When you use the nine questions above, plus references and work samples, you reduce the risk of hiring a talker when you need an operator.
You'll also get better results if you write a clear charter, set a weekly exec cadence, and agree on a 90-day outcome list that strengthens your security posture. Finally, choose a CISO with leadership credibility and a learning mindset, not just tenure, like an evolving learning CISO leader who has spoken at an Executive Summit, with the discipline to keep improving and align with strategic business influencers. Credentials won't do the job alone, but they can signal readiness, especially when paired with proof of execution under governing body oversight, like being certified to lead cyber programs.
FAQ
How long does an interim CISO engagement typically last?
Most engagements run 3 to 9 months, depending on urgency and whether you're hiring a permanent CISO.
What should you pay extra attention to in New York regulated environments?
Focus on evidence, ownership, and reporting cadence to your governing body. Regulators care that you can prove control, not that you bought tools.
How is interim different from fractional?
An interim CISO usually owns day-to-day leadership and decisions for a period. Fractional guidance is lighter-touch, often advisory, and depends on strong internal operators.
How quickly should you expect a 30-60-90 plan?
A credible interim CISO can draft a first version within 5 to 10 business days, then refine it after key interviews to further improve your security posture.
What do you need from your team to support an interim CISO?
You need an exec sponsor, access to decision-makers, and time on calendars. Without that, even the best CISO will stall.
If you're hiring under pressure in New York, set the charter today and schedule the first 10-day checkpoint this week.
