Interim CISO for Acquisition. The 45-Day Plan That Prevents Integration Chaos
Use an interim CISO for acquisition to lock down access, set ready-to-connect guardrails, and deliver a board-ready 45-day integration plan.


Close the deal, shake hands, and then reality hits. You now own a mix of systems, tools, and habits from the M&A you didn't build. Some laptops aren't managed. Some admin accounts don't have MFA. Logging might be spotty. Policies might conflict. Meanwhile, the business wants synergy fast, so teams start connecting networks, sharing files, and granting access.
That's where an interim CISO for acquisition earns their keep. You're not hiring someone to "transform security" in month one. You're bringing in a steady hand to stabilize, sort what matters from noise, and guide integration so you can move quickly without inviting a surprise incident.
The first 45 days decide whether you get speed with trust, or speed with chaos. This plan is built for CEOs, boards, and deal teams who want clear decisions with minimal financial impact, not security theater. You'll walk away with a practical 45-day cybersecurity strategy roadmap, concrete deliverables, and a clear picture of what "good" looks like.
Key takeaways you can use this week
Stop surprise data breaches by locking admin access and stale accounts first.
Name your crown jewels, then protect them before connecting anything.
Get a risk assessment snapshot in days, not months.
Set integration guardrails so teams don't "connect and hope."
Assign owners fast, so decisions don't stall in meetings.
Keep a decision log, so trade-offs stay visible.
Use minimum controls that support safe progress, not perfection.
Give the Board of Directors a one-page update by day 45.
What an interim CISO for acquisition focuses on, and what you should not waste time on
In an acquisition, security work fails when it tries to boil the ocean. A steady-state CISO designs a long-term program, staffing plans, budgets, and multi-quarter roadmaps. That's valuable, but it's not your first need right after close.
An interim CISO for acquisition focuses on triage and decision support for cybersecurity risk. Think of it like bringing in an experienced medic during a storm for strategic guidance. You stabilize the patient, stop the bleeding, and make sure the next steps don't create new injuries. Then you hand off a clear plan for recovery.
This role also differs from a one-time Due Diligence report. Diligence often tells you what's wrong, and sometimes it's already out of date by close. Post-close reality changes daily because access expands, networks get linked, and staff turnover starts. You need someone who can translate risk into actions, sequence work across teams, and keep the integration leader from making "fast" decisions that become expensive later.
A practical interim CISO for acquisition optimizes for three outcomes:
Reduce near-term incident likelihood, especially from identity and endpoint gaps.
Protect deal value, so the acquisition doesn't inherit hidden losses.
Create safe forward motion, so integration doesn't freeze under fear.
Here are two quick contrasts that keep you honest:
Do this: secure admin access, backups, and incident reporting in week one.
Not that: rewrite every policy and launch a company-wide awareness campaign.Do this: set "ready-to-connect" rules before network links.
Not that: connect networks first, then scramble when malware spreads.
If you need an outside leader who can step in quickly, this is the shape of an experienced CISO for hire: business-first decisions, fast stabilization, and clear accountability.
The three questions you need answered in the first week
You don't need perfect answers. You need usable answers.
1) What must not fail?
List the business services and data that keep revenue, care delivery, or operations running. Your output is a short "must-not-fail" service list with owners and dependencies.
2) What is most exposed right now?
Focus on internet-facing assets, identity, endpoints, and remote access. Your output is an exposure list, ranked by blast radius and ease of exploitation.
3) Who owns decisions?
Integration work collapses when ownership is fuzzy. Map decision rights across IT, security, product, legal, HR, and the integration lead. Your output is an owner map (a simple RACI is enough) so approvals don't drift.
Where integration chaos actually comes from
Chaos doesn't come from one big mistake. It comes from small gaps stacking up while people move fast.
Common causes look boring on paper, yet they trigger real incidents:
Identity sprawl happens in Identity Access Management when both companies keep their own directories and "temporary" access becomes permanent. Unmanaged endpoints slip in when acquired staff keep old devices full of technical debt, or contractors join with personal laptops. Unclear logging makes you blind, so you can't tell what changed, or when. Rushed network connections create a shared blast zone. Shadow SaaS appears when teams can't wait for official tools. Mismatched incident response slows down containment because nobody agrees on who calls legal, who talks to customers, or who shuts off access.
Here's a simple scenario you've probably seen. On day 10, a team links networks to "speed up collaboration." Endpoint protection coverage is uneven, and admin accounts aren't reviewed. A single phished credential leads to an attacker moving across both environments. Because logging isn't consistent, you spot it late. Now integration pauses, leaders argue, and the deal team asks why this cybersecurity risk wasn't prevented.
Integration risk isn't mysterious. It's what happens when access expands faster than your ability to see and control it.
The 45-day plan: deliverables, decisions, and the minimum controls that keep you safe
Your goal in 45 days isn't a perfect Information Security Program. It's clear risk control, safe connectivity, and a board-ready view of progress on the Integration Plan. You're building a bridge while people are already walking across it, so you need guardrails first.
This table shows the flow of work in post-acquisition integration.
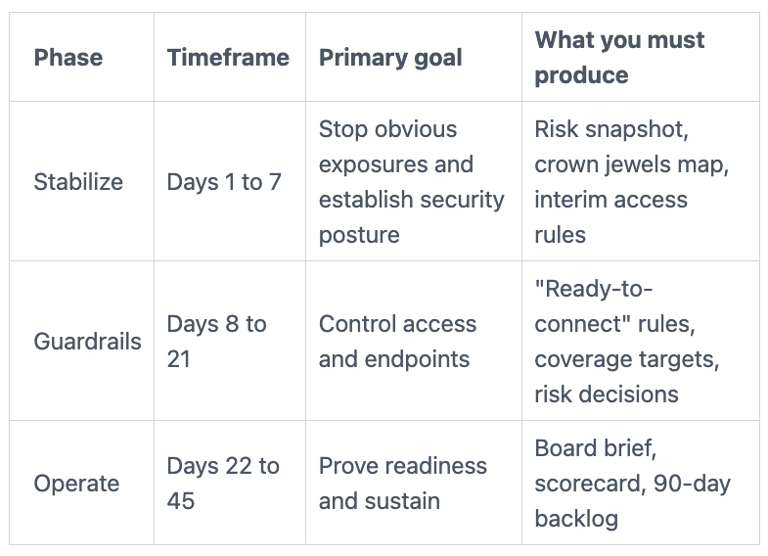
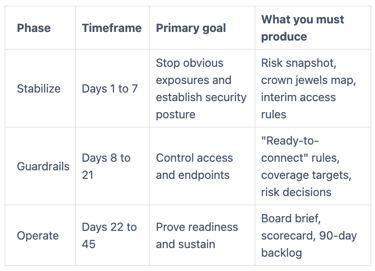
The takeaway: you earn speed by sequencing work, not by skipping it.
Days 1 to 7: Stop the bleeding and get a shared picture of risk
Week one is about shared reality. You need a picture that's "good enough" to make decisions.
Start with a rapid asset and identity inventory. Don't chase perfection. Instead, identify the systems that run core services, who administers them, and how access works. Next, create a "crown jewels" map. Keep it simple: what data matters, where it lives, and how it moves.
Then build a ranked top 10 risk list based on business impact. "High" should mean it can stop revenue, break patient care, trigger reportable exposure, or create major downtime.
Deliverables you should expect by day 7:
A crown jewels map tied to business services
A top 10 risk list from the Risk Assessment with impact, likelihood, and owner
An interim change and access policy (who can approve what, for how long)
A single incident reporting path (one number, one inbox, one escalation)
Quick wins matter because they prevent avoidable pain. Lock down admin accounts, enforce MFA where possible, and disable stale accounts. Confirm backups for critical systems and test at least one restore. Stand up a daily 15-minute cadence with the integration lead, so security decisions match the integration plan.
If you want a simple standard for "qualified leadership under pressure," align on what it means to be a certified CISO ready to lead, especially when frameworks and regulated expectations enter the mix.
Days 8 to 21: Put guardrails on access, endpoints, and data flows
Weeks two and three are about minimum viable coverage. This is where you prevent integration from turning into uncontrolled sharing.
Start with identity and access. Define the SSO direction (even if it's staged), review privileged access, and set a rule for admin creation. Keep a short list of "break glass" accounts, then protect them tightly. If your acquired company has weak joiner, mover, leaver practices, fix the offboarding path early because departures spike after close.
Next, set an endpoint baseline. You don't need every device perfect, but you do need coverage targets that reflect your security maturity and exceptions. Decide your EDR coverage goal for corporate devices, and isolate anything that can't comply yet. Prioritize patching for internet-facing systems, VPN, identity infrastructure, email, and remote management tools.
Email protections often deliver fast results. Tighten phishing defenses, confirm SPF, DKIM, and DMARC where practical, and reduce risky forwarding rules. Then define safe connectivity rules for network and cloud.
Keep this rule simple and visible:
Don't connect networks until you can see and control endpoints and admin access.
This phase also needs a decision checkpoint. For the top risks, you and leadership must choose: accept, transfer (insurance, contract, or vendor responsibility), or fix with a named owner and date. If nobody picks, risk decisions happen by accident.
Days 22 to 45: Integrate with confidence and prove readiness to the board
From day 22 onward, you shift from guardrails to repeatable operations. That's when leaders relax, and that's also when attackers take advantage. So you make "how you run" as clear as "what you block."
Set logging and monitoring minimums for critical services. Decide what must be logged, where it goes, and who reviews alerts. You're not building a perfect SOC in 45 days. You are ensuring the combined company can detect the obvious and respond fast.
Align the incident response runbook across both orgs. Define who declares an incident, who coordinates comms, and who approves containment actions. Then run one tabletop exercise with the integration leader, IT, legal, and HR. Keep it real: stolen credentials, ransomware attempt, or vendor breach.
Also, do a focused Vendor Risk Management and SaaS review for the combined company. You're looking for high-risk vendors, unmanaged SaaS spend, and data-sharing contracts that no longer fit the new reality. This is where acquisitions get surprised by "unknown processors" of regulated or sensitive data.
By day 45, you should have three board-ready outputs:
A one-page risk brief (what changed, what you did, what remains)
An integration scorecard with red, yellow, green status
A 90-day security integration backlog with owners and dates to address compliance requirements and ensure audit readiness
If you want an approach shaped by ongoing education and real execution, work with an evolving CISO with top-tier education who can balance speed, governance, and practical controls.
How you keep leaders aligned when everyone wants different things
In an acquisition, misalignment is normal. Sales wants shared customer data yesterday. IT wants to standardize tools. Legal wants clean answers. HR wants smooth onboarding. Meanwhile, executive leadership wants assurance without getting pulled into technical debates.
You keep alignment by creating a few simple habits that reduce confusion.
First, make decision rights visible. When people don't know who decides, work becomes politics. Second, set a meeting rhythm that matches the tempo of risk. A short weekly executive review beats long monthly meetings that arrive too late. Third, measure coverage and readiness, not activity. Busy teams can still be unsafe.
You'll also need a place to capture trade-offs for strategic guidance. A decision log sounds dull, but it stops selective memory later. When a leader accepts a risk to hit a deadline, you record it with context, duration, and a revisit date. That protects you, and it protects the business.
If your goal is trust, not noise, align your integration with the mindset of a digital trust expert and CISO: clear choices, honest status, and controls people can follow.
Your integration security charter: one page that ends most arguments
A one-page charter establishes foundational security governance as a single source of truth. Keep it in plain language, and get it signed by business and IT leaders.
Include:
Scope (what systems and teams are in play), non-negotiables (MFA for admins, backup checks, incident reporting), risk appetite (what you will and won't accept), and what "ready to connect" means. Add escalation paths, who gets called, and how quickly. Finally, define reporting, including who sees the scorecard each week.
When conflict shows up, you point back to the charter, not to opinions.
The scorecard that shows progress without drowning you in metrics
You don't need 40 metrics. You need a small set that reflects control coverage and response readiness.
A practical scorecard includes:
MFA coverage for admin accounts, EDR coverage for corporate endpoints, critical patch SLA performance, backup success for key systems, logging coverage for critical services, number of open high-risk findings, and time to revoke access after departures. Review weekly, then roll up a red, yellow, green view for the Board of Directors.
FAQs about using an interim CISO for acquisition
Executives tend to ask the same questions right before or right after close in M&A. Here are clear answers you can use.
FAQs to include
When should you bring in an interim CISO, pre-close or post-close?
Pre-close, especially during due diligence, helps you shape integration terms and spot deal-killers early. Post-close is where most damage happens, so immediate stabilization matters. If you can only choose one, start at close or day one post-close.
What is the difference between an interim CISO and a fractional CISO?
An interim CISO usually means you need a leader now, with higher weekly time and clear near-term deliverables. A fractional CISO often fits steady oversight when the pace is slower. A virtual CISO is a related term for outside leadership providing similar flexible support. In acquisitions, an interim CISO is common because the transition period's first weeks are intense.
How do you work with the existing IT leader and security team?
You clarify decision rights, then support the team with security diligence, focus, and sequencing. You don't replace their knowledge of systems. Instead, you remove ambiguity and unblock fast, safe actions.
What deliverables should you expect by day 45?
By day 45 of the transition period, expect a risk snapshot, guardrails for access and connectivity, a shared incident runbook, and a 90-day backlog with owners. You should also get a board-ready one-page brief and a simple scorecard.
How do you handle regulated data (HIPAA, PCI, SOX) during integration?
You start by identifying where regulated data lives and who touches it, while assessing the information security program. Then you set interim controls that prevent uncontrolled access and uncontrolled data flows, all while meeting compliance requirements. Coordinate early with legal and compliance, and avoid making promises you can't verify yet.
Should you connect networks right away?
Not unless you can control admin access and see endpoints on both sides. A rushed connection often turns one company's problem into everyone's problem. Stage connectivity based on "ready-to-connect" criteria.
What does success look like for the board?
The board should see reduced cyber risk exposure, with fewer unknowns, clear ownership, and a dated plan. They should also see that the business can detect and respond to incidents during integration, not after damage spreads.
Conclusion
Acquisitions reward speed, but speed without control creates expensive surprises that can erode company valuation. When you use an interim CISO for acquisition, you create order fast: you name what must not fail with a clear cybersecurity strategy, reduce the most likely exposures, and set guardrails that keep integration moving. Just as important, you give leadership a clean set of decisions, with owners and dates, so risk doesn't hide inside "temporary" workarounds.
If you're within days of close (or already feeling integration strain), validate your 45-day plan now. Schedule an advisory conversation, get an integration risk snapshot, and make sure your team is building program momentum with trust, not wishful thinking.
