Interim CISO in Maine: The Fastest Way to Reduce Risk While You Keep Growing
Hire an interim CISO in Maine to lock down identity, tighten vendor access, test restores, and set a 30-90 day risk plan while you grow.


Growth in information technology management has a way of multiplying your risk. One new system turns into five. One key vendor turns into a web of third parties. Your team adds remote staff, more data moves to the cloud, and customer expectations climb. Meanwhile, security leadership time stays flat. That's when small gaps start to feel like landmines.
An interim CISO in Maine, a Chief Information Security Officer, is a cybersecurity consultant Maine you bring in now, for a set period, to stabilize risk and set direction. You're not hiring a permanent executive on day one. You're getting experienced leadership quickly, with a clear start and finish, so you can keep moving.
If you're in Maine healthcare cybersecurity, finance, manufacturing, higher ed, or a Maine-based company with regional suppliers and distributed teams, the pattern is familiar. You need clearer risk, fewer surprises, stronger customer trust, and a plan that fits how you actually work. The goal is simple: reduce risk fast while keeping momentum.
Key takeaways you can use this week
These information security leadership insights offer practical steps you can implement right away.
Fix identity first: Close MFA gaps, lock down admin access, remove old accounts.
Pick your "crown jewels": Agree on the few systems and data sets that can't fail.
Turn fear into a short risk list: 10 items, each with an owner and due date.
Test one restore: Prove you can recover, not just that backups exist.
Make vendors earn access: Tighten third-party logins and document who has what.
Ask for one-page reporting: Tie risks to your information security strategy, money, uptime, and customer impact.
Define the first 30 days: Discovery, quick wins, and an incident-ready baseline.
Choose the right model: Interim IT executive for urgent change, fractional for steady guidance, full-time for ongoing complexity.
These tactical steps lay the groundwork for security program development.
When an interim CISO is the fastest path to lower risk
You usually don't need an interim CISO because you "care about security." You need one because business pressure exposed a leadership gap that interim security leadership can address swiftly. Your IT leaders may be strong, but they're often buried in uptime, projects, and tickets. Security then becomes a side job, and side jobs don't hold up under audit pressure or an incident.
Common triggers look like this:
A customer sends a security questionnaire that reads like a contract. Cyber insurance renewal asks for proof, not promises. An auditor flags weaknesses during a cybersecurity risk assessment, and no one can explain the plan. You discover tools you pay for but don't use well. Patch and vulnerability work feels random. Vendor access has grown messy. And on top of all that, you worry about ransomware because your incident plan is either untested or missing.
Interim leadership works when you need fast clarity and fast decisions. You get a risk management executive who can translate technical issues into business risk, settle ownership questions, and drive action without waiting for a long hiring cycle in the Portland Maine IT jobs market. If you want to see what that level of leadership looks like, start with this page on an experienced interim CISO for hire.
Clear signs you need help now, not later
If several of these are true, you're already paying for the gap, just not on an invoice:
You had a recent incident, near miss, or "we got lucky" moment.
A cyber insurance renewal is coming, and you can't answer the controls questions.
A major customer or partner asked for a security review you can't complete fast.
Audit findings repeat, or remediation dates keep slipping.
Ownership is unclear (security is "IT's job," but no one is accountable).
You're hiring quickly, adding remote staff, or expanding locations.
You're moving to a new cloud platform, ERP, or patient or student system.
You're worried about ransomware, but you haven't tested recovery.
You don't have a current incident response plan, or you've never run a tabletop.
Security reports don't make sense to executives, so nothing gets funded.
Too many high-risk vendors connect to sensitive data or core systems.
Interim vs fractional vs full-time CISO, how to choose without overbuying
The right choice depends on urgency and complexity, not on what feels "proper."
Here's a simple comparison to keep the decision practical:
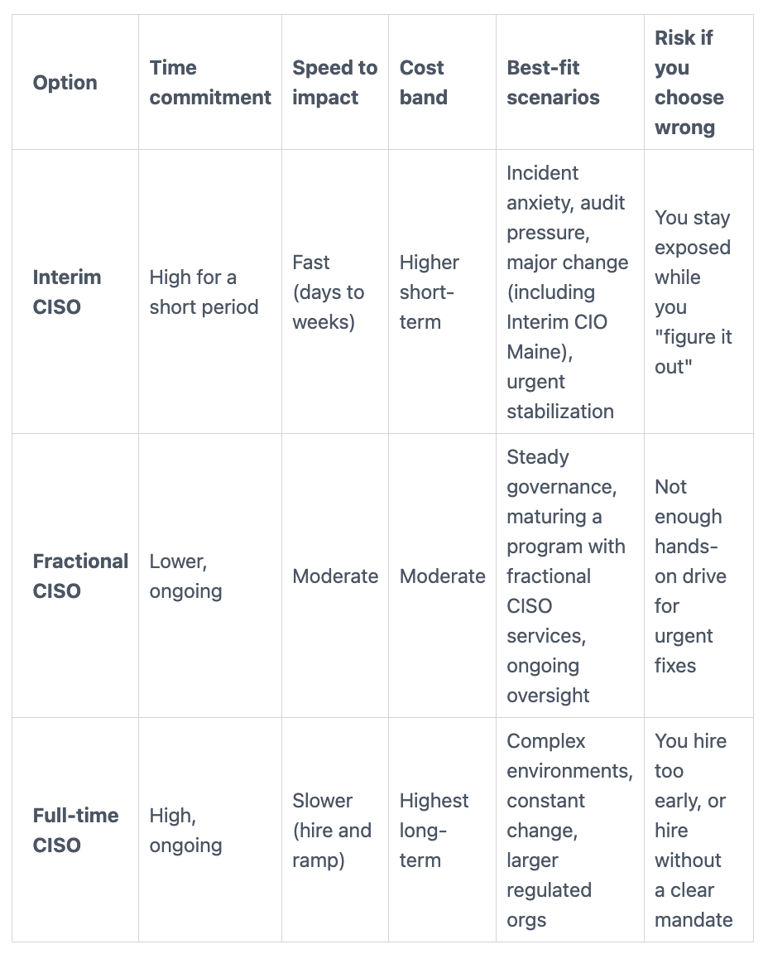
Interim is the "get control now" option. Fractional is "keep it moving without heavy lift." Full-time is "this is a permanent executive function here." Your goal is to match coverage to risk and pace of change.
What you should expect in the first 30 to 90 days
You shouldn't expect a tool shopping spree. You also shouldn't expect a 12-month policy rewrite. The best early work is focused, visible, and tied to outcomes as part of your information security strategy: reduce the chance of a serious incident, improve recovery confidence, and give leadership a plain-language plan.
Under cybersecurity leadership in Maine, you often run lean teams with mixed environments. You might have a small IT staff, an MSP, some legacy systems that still matter, and modern cloud services layered on top. Remote work and regional vendors add more access paths, which adds more risk if you don't control identity and oversight.
A strong 30 to 90-day approach creates artifacts you can use, not slide decks that age out. You should walk away with a clear risk view, a prioritized roadmap, an incident plan your leaders understand, and a small set of metrics that hold up in a board meeting. For more executive-friendly perspectives on that kind of work, you can also browse these CISO insights on business cybersecurity.
If your plan needs perfect data to start, it's too slow. You can reduce real risk with "good enough" facts and clear ownership, as a Chief Information Security Officer would advise.
Days 1 to 15, get the facts, stabilize the highest risk items
First, you establish what matters most. That means mapping critical systems, IT infrastructure security, "crown jewel" data, and the business processes that can't stop (payroll, patient care, production, student services, shipping, billing). At the same time, you confirm who owns what, including MSP responsibilities in information technology management and internal decision rights.
Next, you handle quick wins that reduce common attack paths without disrupting operations. That usually includes closing MFA gaps, tightening admin access, removing stale accounts, confirming backup coverage, and checking whether restores actually work. You also look at patching cadence on the assets that matter most, plus basic logging and information security operations so you can investigate events later.
The theme is speed with care. You keep projects moving, but you stop obvious bleeding.
Days 16 to 45, turn chaos into a simple risk plan everyone can follow
Once you've gathered enough facts, you translate technical findings into a short risk register from a cybersecurity risk assessment tied to business impact. Not "critical CVE on server X," but "risk to production uptime" or "risk to regulated data." Each risk gets an owner, a target date, and a realistic path to reduce exposure.
Then you run an executive readout that doesn't overwhelm. You focus on tradeoffs and choices: what to fix now, what to schedule, what to accept, and what needs budget. Instead of endless committees, you set a light cadence (often a weekly checkpoint) to remove blockers and keep work on track.
This is also when vendor risk becomes a real workflow. You define what "approved vendor access" means, how vendors request it, and how access gets reviewed and removed.
Days 46 to 90, build repeatable security, not hero work
By this phase, you shift from urgent fixes to repeatable habits. Policies become short and usable under information security governance. Project teams get simple security steps that match the way they ship work. Vendor intake becomes consistent. Training becomes realistic, so people actually complete it and remember it.
You also align to a framework such as NIST or ISO in plain terms. Think of it as a map. It helps you see what's missing and what's working. It's not a certification sprint, it's a way to prioritize and explain progress.
This is where trust starts to feel real to customers and leadership. If you want a clear view of what "trust" looks like at the executive level, read more about a digital trust expert and CISO.
How you make security a growth enabler in Maine, not a blocker
When security feels like a blocker, it's often because it shows up late, speaks in jargon, or asks for effort without clear payoff. Your goal is the opposite: strategic security planning that helps you sell, operate, and partner with confidence.
In practical terms, that means fewer surprises during customer reviews, cleaner answers for cyber insurance, and fewer outages caused by preventable issues. It also means you can say "yes" faster, because you've defined the safe way to do things. For Maine organizations with regional suppliers, seasonal staffing, or remote teams, clarity beats complexity every time.
Boards also benefit. Instead of vague heat maps, you bring a small set of metrics that show direction and ownership. You make it easy to govern, because leaders can see what's improving and what isn't. That's how security supports growth without slowing the business.
The metrics and reporting your board and customers actually care about
Board reporting should fit on one page, making it easy for your Chief Technology Officer Maine to stay informed. If it can't, it's probably not decision-ready.
A useful set of measures includes:
Top critical risks with owners: What could hurt revenue or uptime, and who's fixing it.
Incident readiness status: When you last ran a tabletop, and what changed after.
Backup restore testing: Proof of recent restores for key systems.
Phishing resilience trend: Not blame, just trend lines and coaching follow-through.
Patching on critical assets: A simple view of what's current and what's late.
Vendor risk posture: Which vendors have sensitive access, and how your Data protection officer reviews them.
Security debt burn-down: Old risks you're removing from information technology management, not just new tasks you add.
Time to detect and respond: Whether you can see and contain issues faster over time.
How you hand off cleanly so you are not dependent on one person
Interim work should end with strength, not dependence. That means you get a documented roadmap, clear roles and responsibilities, and runbooks for the work that must happen every week or month. You also get notes on tool rationalization, budget priorities, and what you can stop doing because it doesn't reduce risk.
If you decide to hire a permanent leader, an Interim IT executive can help you define the role, screen candidates like an Information services director or Senior cybersecurity manager, and onboard the right person faster. If full-time isn't needed yet, you can also transition to lighter ongoing coverage after stabilization. The handoff works best when it's backed by continuous learning and disciplined leadership, like what's described in this page on an evolving CISO committed to continuous learning.
FAQs about hiring an interim CISO in Maine
FAQ prompts to cover
How fast can you start, and what do you need first?
You can often start within days. First, you need access to key people, system lists, current policies (if any), and recent audits or incident notes.
In executive leadership recruitment, what does an interim CISO do that my IT leader cannot right now?
You get focused leadership on risk, governance, and incident readiness, without pulling your IT leader away from operations and delivery.
How do you work with existing MSPs, internal teams, and Augusta Maine cybersecurity providers?
You set clear ownership, tighten access, and create simple operating rhythms. You don't replace teams, you help them perform with less confusion through remote CISO opportunities.
Do you help with NIST, ISO, HIPAA, PCI, SOC 2, or regulatory compliance Maine?
Yes, as a practical readiness path tied to your business goals. You use frameworks as structure, not as paperwork.
How do you support incident response and ransomware readiness?
You confirm backup recovery, tighten identity controls, improve detection basics, and run a tabletop so leaders know their roles.
How do you price interim work (retainer vs fixed scope)?
Both can work for Virtual CISO Maine. Retainers fit uncertain environments, fixed scope fits well-bounded outcomes. Either way, as a hybrid security executive, you should see clear deliverables.
For credibility that stands up in board and audit conversations, it also helps to work with a leader who is CISSP-certified and ready to lead.
Conclusion
You don't need a perfect program to get safer fast. You need clear leadership, a prioritized view of risk, and a plan your teams can execute without stalling growth. An interim CISO gives you that structure quickly, then leaves you with repeatable habits and a clean handoff.
If you're weighing an interim CISO in Maine versus an Interim CIO Maine, fractional, or full-time coverage, your next step should be simple. Schedule a short call to confirm fit, align on what the first 30 days should produce, and decide which model matches your risk and pace of change. The right choice (a Chief Information Security Officer) reduces surprises while you keep building.
