Thoughts About CISO Security Resources: 7 Pitfalls That Turn "More Tools" Into More Risk
CISO Security Resources can backfire when tools pile up. Spot 7 pitfalls, assign owners, cut alert noise, and reduce risk without more tools.


For the Chief Information Security Officer, buying another security tool feels like progress, especially in the first 100 days. You get a new dashboard, a new contract, and a new sense of control. Yet many organizations become less safe as the cybersecurity stack grows, because complexity breeds gaps, fatigue, and unclear ownership, fueled by emerging technologies like artificial intelligence.
If you're a CEO, board member, or CISO, you don't need more noise. You need simpler proof that risk is going down, readiness is going up, and the business can recover fast. That starts with being honest about what "CISO Security Resources" really are: your people, time, budget, tools, data, and operating rhythm that reduce business risk.
A good program moves from checklists to trust outcomes, like uptime, customer confidence, and fewer surprises. The mindset shift described in From compliance burden to customer confidence applies here too. You're not collecting tools, you're building capability.
This article gives you 7 practical pitfalls to spot early, plus what to do instead without a massive rebuild.
Key takeaways you can use this week
If a tool doesn't reduce one agreed business risk, pause the purchase. In risk management, nice features don't count.
If you can't name one accountable owner for a capability, you don't own it. Assign ownership before renewal.
If alerts exceed your team's daily capacity, you're operating blind. Artificial intelligence-assisted tuning is risk reduction.
If integrations aren't tested with real scenarios, assume they don't work. "Connected" is not the same as "usable."
If the stack needs heroics to run, simplify it. Complexity is an attacker's friend.
If you can't explain progress in plain language, expect budget whiplash. Use executive-friendly cybersecurity metrics to keep security strategy decisions stable.
If your operating model is unclear, tools will fill the void. Write down the rhythm, roles, and evidence your stakeholders expect monthly.
Before you buy, get clear on what your CISO Security Resources are meant to achieve
Tools are inputs. Outcomes are what the business feels. When you're clear on outcomes, your stack becomes smaller, calmer, and easier to defend.
"Good" usually looks like this: cyber resilience beyond basic defense, fewer critical risks, faster detection and containment, cleaner reporting to leadership, and simpler operations. In other words, you spend less time debating vendor features and more time reducing exposure.
A lightweight decision frame keeps you honest:
Top business risks (downtime, fraud, data exposure, safety, regulatory impact)
Governance
Target capabilities you must be good at (identity, backup recovery, detection)
Current gaps you can prove (not guessed)
Total cost to run (people hours, tuning, integrations, on-call, vendor management)
Here's a board-friendly example. If ransomware is a top risk, the outcome isn't "we bought EDR." The outcome is "we can restore crown-jewel services within the agreed time, even on a bad day." If third-party risk is a top risk, the outcome is "we can identify critical vendors fast, and we can prove contract and access controls work."
If you need help aligning your security strategy to business strategy, governance, and business alignment, the perspective in Signs of silent cyber risks for CEOs is a useful reference point.
Separate what you own from what you can actually run
A license isn't a control. It's a box of parts.
Operating security tools takes real hours: integration work, rule writing, tuning, triage, exception handling, access reviews, patch coordination, and vendor management. Even "easy" tools create ongoing chores, especially when your environment changes weekly.
You're likely over-extended if you see these signs:
Backlogs that never shrink (vulns, detections, access requests, policy exceptions)
Noisy alerts that train your team to ignore "high severity"
Tribal knowledge (one person knows the rules, the parser, the workflow)
Skipped hygiene (stale agents, overdue reviews, untested restores)
If you can't run it calmly, you can't trust it in a crisis.
Use a simple "capability map" so the stack serves the plan, not the other way around
A capability map scorecard provides decision support that is plain and boring, which is why it works for your security program. It keeps you from buying overlapping tools that nobody owns.
Start with a short list most boards understand: asset inventory, identity, endpoint, email, vulnerability management, logging, detection and response, and backup and recovery. Then map each tool to one primary capability.
To make it operational, tie each capability to three things:
One owner (a person, not a team)
One metric (trend over time, not a one-time score)
One runbook (what you do when the tool signals trouble)
When you do this, your stack stops being a pile of products. It becomes a set of run-able systems, with clear accountability and evidence.
The 7 pitfalls that turn "more tools" into more risk, and what to do instead
Tool sprawl doesn't fail loudly. It fails quietly, through gaps, confusion, and false confidence. These pitfalls show up in growing companies, post-merger environments, and any place where tool buying got ahead of cybersecurity operating.
Pitfall 1: You buy for features, not for an agreed risk reduction outcome
What it looks like: "Best of breed" becomes "best at demos." Each team picks its favorite tool, then asks the CISO to bless it.
Why it increases risk: You spend money without reducing your top exposures. Adoption stays shallow, so coverage is patchy.
Fixes that don't require a rebuild:
Write down your top 3 risks and the business impact (hours of downtime, fraud loss, customer churn).
Choose 2 to 3 outcome metrics (time to detect, time to contain, coverage of crown jewels).
Require an adoption plan: owners, training time, tuning time, and a 60-day checkpoint.
Pitfall 2: You create alert overload, then miss the real incident
What it looks like: SIEM and EDR generate constant "high" alerts. People close tickets to survive the day.
Why it increases risk: Fatigue becomes policy. Meanwhile, leadership assumes "we're monitored," even as real signals get buried.
Fixes that don't require a rebuild:
Tune detections to crown jewels and identity abuse paths first, aligned with MITRE ATT&CK to prioritize adversary behavior.
Set clear severity rules and escalation paths, including after-hours coverage.
Automate low-risk closures and enrich alerts before they hit humans.
If you want a clean model for crisis-ready signal and reporting, see command center metrics for cyber crises.
Pitfall 3: Your tools are not integrated, so attackers live in the gaps
What it looks like: Identity logs sit in one place, endpoint data in another, cloud events in a third, and email protection in a fourth. Correlation becomes guesswork.
Why it increases risk: Attackers move between seams. Your team wastes hours stitching evidence together during incident management.
Fixes that don't require a rebuild:
Pick a primary detection plane (often identity plus endpoint) and make it reliable first.
Standardize logging and retention for critical systems with threat intelligence.
Validate integrations with test cases, not vendor claims.
Integration is a cybersecurity control, not an IT nice-to-have.
Pitfall 4: You outsource "ownership" to vendors, then nothing is truly accountable
What it looks like: "The MDR has it," or "the vendor manages that." Yet nobody can explain the runbook, the decision rights, or the proof.
Why it increases risk: Managed services can run tasks, but they can't own your business decisions. Shared responsibility turns into shared confusion.
Fixes that don't require a rebuild:
Assign one internal owner per capability, even if a vendor does daily work.
Define SLAs and decision rights, including when to wake up executives.
Run monthly service reviews with evidence (cases, response times, tuning changes).
This ties directly to readiness and governance described in board oversight for incident response.
Pitfall 5: You underfund the people and process needed to operate the tools
What it looks like: You buy platforms, but you don't fund engineering time, on-call, training, or workflow design. Backlogs grow, audits hurt, and morale drops.
Why it increases risk: Tools drift out of tune. Agents go stale. Exceptions pile up. Then risk hides in plain sight.
Fixes that don't require a rebuild:
Budget for operations and cybersecurity experts: engineering time, tuning, and coverage, not only software.
Simplify the stack where overlap exists, and reinvest in runbooks.
Use interim support when hiring is slow, so momentum doesn't die.
If leadership capacity is your bottleneck, Fractional CISO for rapid control can be a practical bridge.
Pitfall 6: You expand your attack surface with poor configuration, access, and integrations
What it looks like: Too many admin roles, long-lived API tokens, wide connectors, and default settings left in place, including in Industrial Control Systems for critical infrastructure. Tools become new doors.
Why it increases risk: Attackers love "trusted" paths: admin consoles, integrations, and service accounts. A cybersecurity tool compromise can become a platform compromise.
Fixes that don't require a rebuild:
Enforce least privilege and separate admin accounts for cybersecurity platforms.
Use basic secrets management and rotate tokens on a schedule.
Run quarterly access reviews and configuration baselines for the cybersecurity stack itself.
Pitfall 7: You cannot prove value, so the program becomes unstable and reactive
What it looks like: Reporting is either too technical or too vague. Budget decisions swing, and leaders swap tools instead of fixing the operating model.
Why it increases risk: Instability creates gaps. Teams chase the next purchase while foundational controls lag.
Fixes that don't require a rebuild:
Pick a small, stable set of board-friendly metrics and show trend lines.
Tie spend to reduced exposure and faster recovery, in hours and dollars.
Make tradeoffs explicit as part of your security strategy, so "stop doing" items free capacity.
A solid approach is outlined in measuring cybersecurity's business impact.
How to right-size your security stack without losing coverage
Right-sizing isn't about buying less. It's about operating what you have with discipline. As the CISO, align your security stack with strategic priorities. In the next 30 to 90 days, you can reduce complexity while keeping protection steady, sometimes improving it.
Progress should feel boring: fewer surprises, fewer urgent escalations, and clearer decisions. Your board should see calmer reporting, not bigger slide decks.
Run a 30-day stack reality check, then freeze new purchases for a short window
Treat this like a sprint. As CISO, inventory tools, owners, costs, integrations, and actual usage. Then assess data quality (are logs complete, are agents healthy, are alerts tuned). Capture the human load too: hours per week to run each capability.
Next, set a short purchase pause. Freeze new tools for 30 days while you tune, integrate, and retire overlap. Document exceptions and risk acceptance so urgency doesn't become chaos.
Make tool decisions using a simple scorecard your board of directors can understand
Use a plain scorecard to keep decisions consistent. Here's a simple template you can reuse in board of directors audit and risk committee updates.
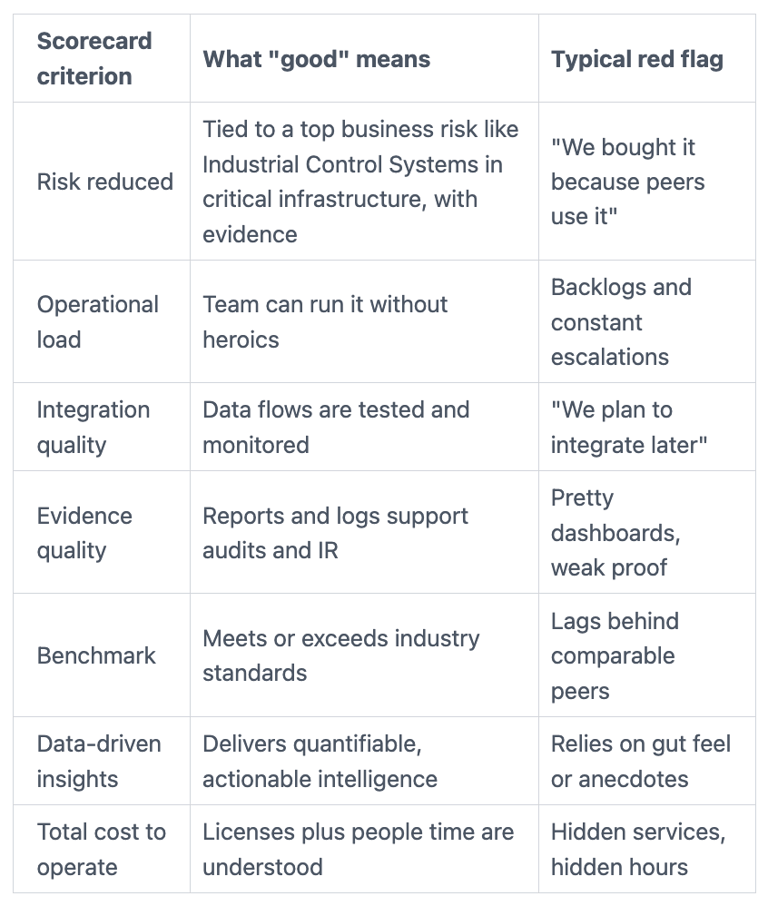
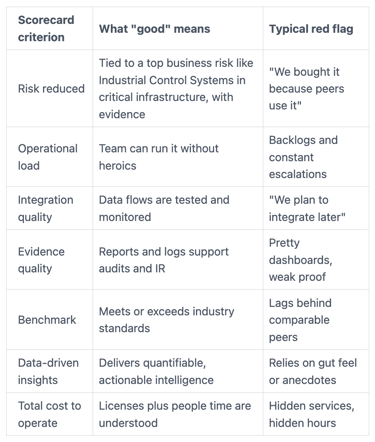
The point isn't perfection. It's shared language. If you want stronger oversight questions that fit this scorecard, use Audit committee cyber risk questions as a guide.
FAQs leaders ask about CISO Security Resources and tool sprawl
How do you know when you should consolidate tools?
Consolidate when overlap creates noise, and nobody can own the seams. Keep best-in-class only where it clearly reduces a top risk.
How many security tools is too many?
It's too many when your team can't patch, tune, and review access on schedule. Tool count matters less than your ability to run the stack calmly.
How is artificial intelligence fueling tool sprawl?
The explosion of artificial intelligence-powered security tools is contributing significantly to sprawl, as teams rush to adopt the latest innovations without assessing overlaps.
Should you choose an MDR to simplify operations?
MDR can help simplify cybersecurity operations, but only if you keep internal ownership, runbooks, and decision rights. Otherwise you outsource accountability, not just tasks.
What should you measure to prove the stack is working?
Track a few trends: time to detect, time to contain, restore test success, crown-jewel coverage, and critical exposure windows. Keep the set stable.
Is it ever smart to keep a tool you barely use?
Only if it covers a risk you can name, and you can fund adoption within a clear time box. Otherwise, retire it and remove the clutter.
How do you build a team to tackle tool sprawl?
Invest in professional development while monitoring compensation trends to attract and retain talent equipped to manage the security stack effectively.
When the stack is messy, how do you evaluate security leadership?
Look for decision-making and operating discipline in the CISO's leadership role, not tool vocabulary. A helpful reference is how CEOs should vet a CISO.
Conclusion
More tools don't automatically mean less risk. The seven pitfalls usually come down to the same pattern: unclear outcomes, noisy operations, weak integration, and fuzzy accountability. When you anchor your CISO Security Resources to business results, assign real owners, and measure what leadership understands, the stack gets simpler and stakeholders' trust gets stronger.
Pick one pitfall that fits your world right now. In your first 100 days, run the 30-day reality check, then stabilize reporting around business risk, recovery, and cyber resilience following best practices. If you want experienced support tightening priorities, ownership, business alignment, and board-ready evidence, start with engage a CISO advisor.
